- Google Cloud Security
- Community Blog
- Supercharge Your Security Visibility with Chrome E...
Supercharge Your Security Visibility with Chrome Enterprise and Google Chronicle
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
You already know Google Chronicle is a great SIEM. It can help you identify and respond to security threats, and it can give you a comprehensive view of your security posture. But did you know that by integrating Chrome Enterprise with Google Chronicle, you can get even more out of your security investment, and you don't have to pay a penny for it? Now I have your attention. Let's look at Chrome Enterprise and see how it can boost your security visibility.
This is the first part of a multi-part blog series on how to integrate Chrome Enterprise with Google Chronicle. In this part, we will discuss how to integrate Chrome Enterprise with Google Chronicle to boost your security visibility. In future parts, we will explore other use cases for this integration, such as identifying and responding to security threats, and getting a comprehensive view of your security posture.
Google Chrome is the most popular web browser in the world without a question. More than two billion people already use Google Chrome for work and play. But what many don't know is that Chrome can also be used as a powerful security tool. With Chrome’s cloud-based management tool you can control how Chrome is used on your devices regardless of the OS and gather security insights about your fleet.
Let's see some of the benefits of using Chrome Enterprise Management:
- Central management and visibility across operating systems: Chrome Enterprise allows you to apply extensive Chrome policies across platforms and OS versions, all from the Google Admin console (Chrome Browser Cloud Management). You can restrict access to certain websites, enforce password policies and more. This gives you a single tool to manage security policies and gain greater visibility into your browser fleet.
- User management: You can use Chrome Browser Cloud Management to manage users' Chrome behavior via cloud-based policies when they sign into their browsers. This allows companies to enforce Chrome policies when users sign in to corporate accounts on unmanaged devices.
- Proactive threat defense: Chrome has built-in protections to help safeguard your organization from external threats and user error. These protections include Google Safe Browsing, sandboxing, and site isolation.
- Control over extensions: Security practitioners often find it difficult to obtain information about extensions, such as which ones are installed, which versions are in use, and what permissions are required to run them. This is often because this information is not easily accessible through software packaging tools like Intune and JAMF. Chrome Enterprise, on the other hand, gives you control over extensions, including visibility into versions, last update time, developer information, privacy policy, risk assessments, permissions and more.
- Reporting: Chrome Browser Cloud Management provides detailed reports on how Chrome is being used on your devices. You can use these reports to identify potential security threats and track user activity.
The beautiful part of all the things mentioned above is that they can be done without additional cost. You can accomplish all of them without having to reinstall Chrome since you can bring user-installed instances of Chrome under management seamlessly.
Get Chrome security event information via integration with Google Chronicle
On top of the no cost features of Chrome Enterprise Management, let's talk about how you can import Chrome Enterprise data into Chronicle to improve your visibility.
As a prerequisite to leverage Chrome integrations into Chronicle, you will need to enroll Chrome into the Admin Console in order to access reporting information. Enrolling browsers is very easy. For help getting started, the Beyond Browsing YouTube playlist is a fantastic resource. You can also contact our team here.
If you prefer to read technical documentation, you can read the Chrome Browser Cloud Management guide or follow the step-by-step guides in your Google Admin Console.
After you have completed the Chrome Browser Cloud Management setup and enrolled your endpoints, Chrome events will be collected. The data is logged in the Google Admin console under Reporting > Audit and investigation > Chrome log events.
Here are some of the events that were captured:
|
Event value |
Description |
|
Malware transfer |
The content uploaded or downloaded by the user is considered to be malicious, dangerous, or unwanted. |
|
Extension install |
A browser extension was installed, either by user action or by the administrator. |
|
Password changed |
The user resets their password for the first signed in user account. |
|
Password reuse |
The user has entered a password into a URL that’s not included in the list of allowed enterprise login URLs. |
|
Unsafe site visit |
The URL visited by the user is considered to be deceptive or malicious based on Google Safe browsing |
For more information on all Chrome events, please see the Google support documentation:
https://support.google.com/a/answer/9393909.
A connector is a way to connect Google Admin Console to other systems, including Chronicle. To set up the Chronicle connector, you will need to contact your Google Customer Engineer or request an Ingestion API key from Google Chronicle support. Once you have your Ingestion API keys, we can start configuring Chrome Enterprise to send logs to Chronicle where they will be normalized, enriched, and indexed. All data in Chronicle, by default, is searchable for a year.
To configure Chrome Enterprise to send logs to Chronicle, you can follow the instructions below.
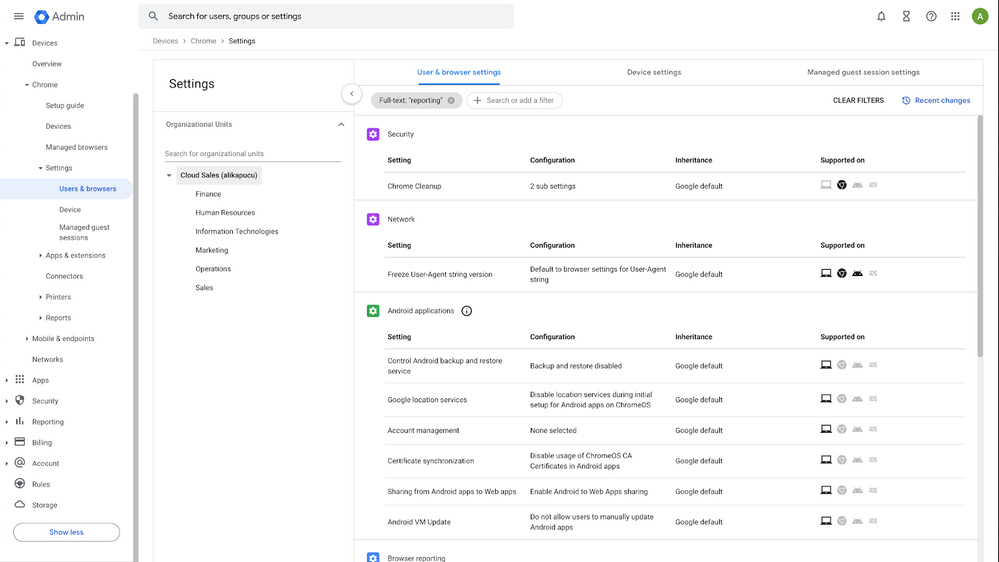
- Log in to the Google Admin console at admin.google.com: https://admin.google.com/
- Navigate to Devices > Chrome > Settings > Users and browsers.
- Select your top-level organizational unit, so that all child organizations will inherit the policy.
- Scroll down to Browser reporting.
- Set Managed browser reporting to Enable managed browser cloud reporting.
- Set the frequency of Managed browser reporting uploads to your preferred value. I set my demo environment to 6 hours. It’s worth noting that security events are transmitted in real-time between Google Chrome and Chronicle.
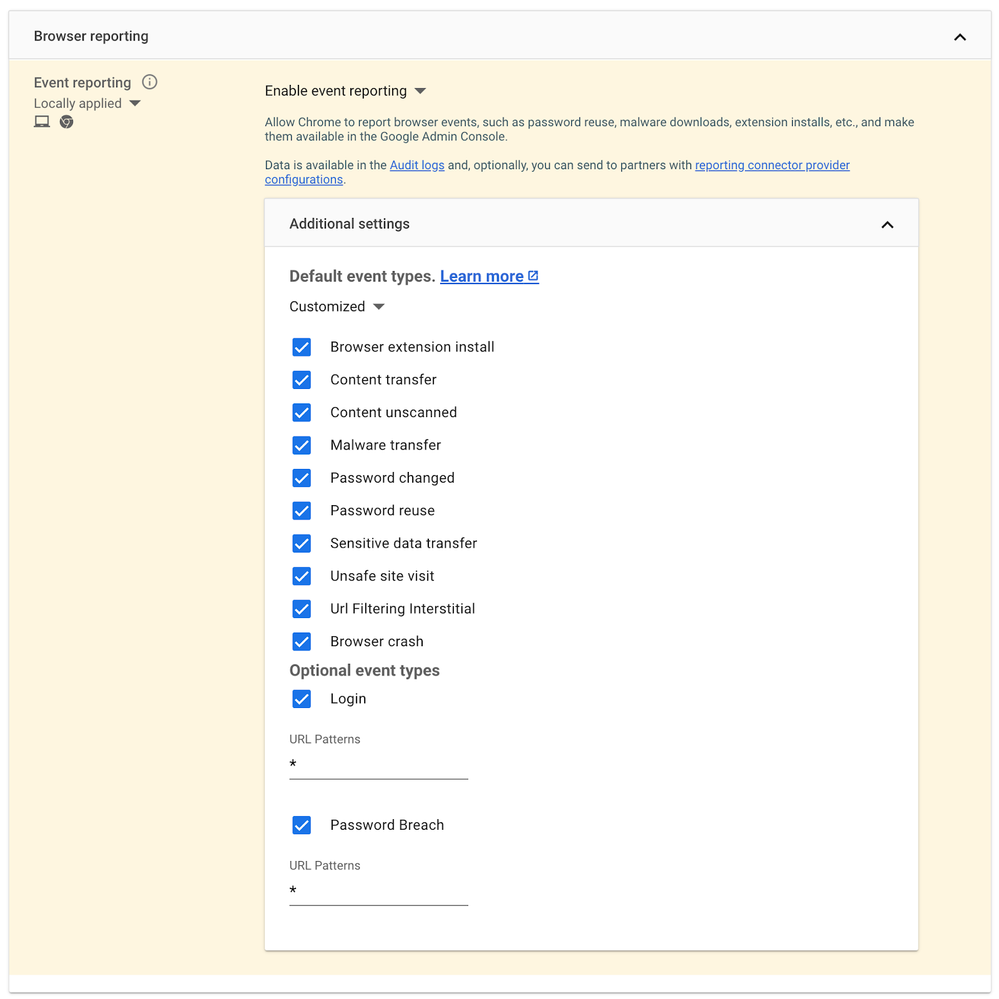
Additionally, you can also customize the events you would like to report to Chronicle - Now that the events are turned on, let's configure the Chronicle connector under Devices > Chrome > Connectors.
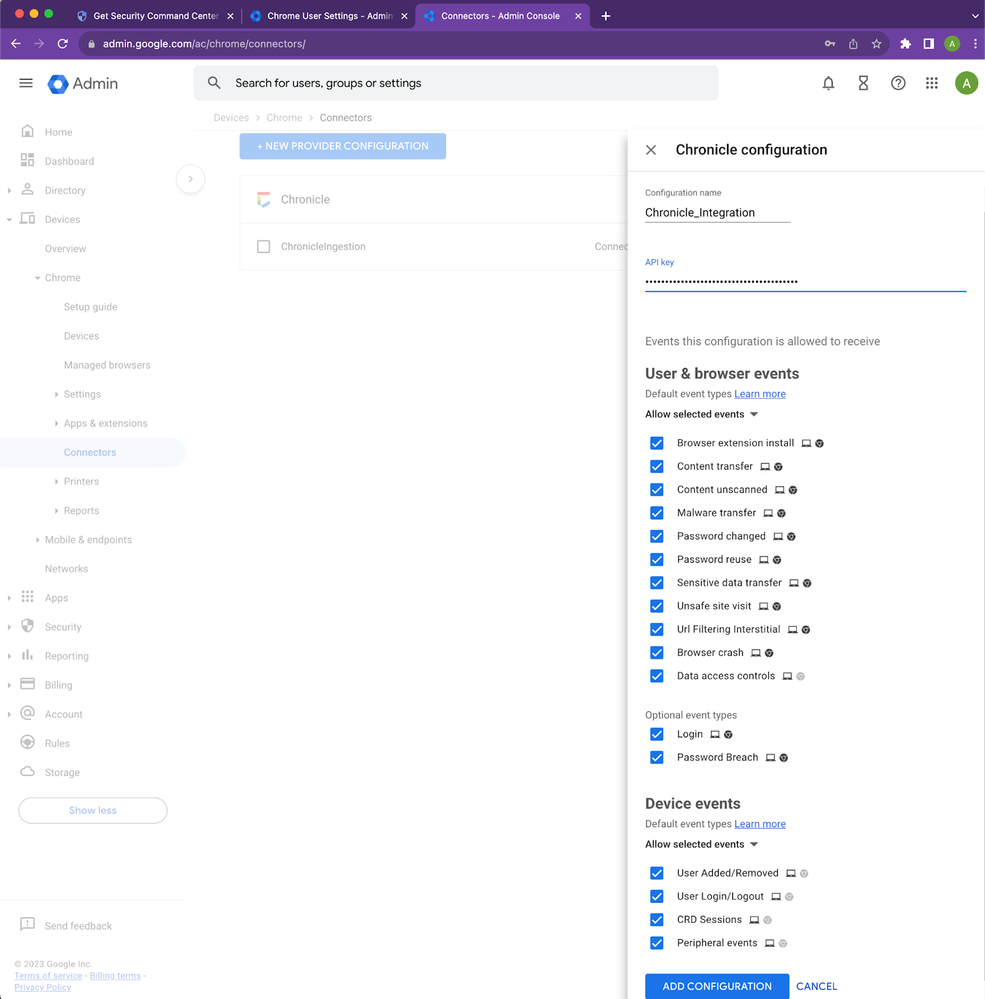
- Click the New Provider Configuration button and select Chronicle as the provider.
- Enter the configuration name that you want this connector to display as in the Google Admin console.
- Enter the API key value you received from Chronicle Support or your Google customer engineer.
- Enter the endpoint host name malachiteingestion-pa.googleapis.com. You can find other regional endpoints in the link below.
https://cloud.google.com/chronicle/docs/reference/ingestion-api - You can forward all the events or pick and choose which ones you want to forward to Chronicle
- Press the "Add Configuration" button to save.
- Select the Organizational Unit in which the reporting events are enabled and select the Chrome Chronicle connector that was created in the previous step, and click Save.
(Note that some event types may require BeyonCorp Enterprise licensing and/or password manager usage. To learn more, check out the documentation )
After you apply the policy in Chrome Browser Cloud Management, alerts from managed browsers will be sent to Chronicle. The ingested events include fields such as accessed domain, downloaded file hash, and username. You can find each of these in Chronicle with the methods below:
- Search & Investigative Views: You can directly enter username, hash, domain, and IP values into Chronicle's search bar and see the results in the respective investigative views, which are converted into Unified Data Model (UDM) events with enriched data immediately after the ingestion.
- Chronicle Rules: You can use Chrome event data to create or enhance existing threat detection rules. This lets you automatically detect and investigate threats, including unusual or suspicious events that haven't tripped any alerts in Workspace. Chronicle delivers more value by enabling you to compare events telemetry with activity in other logs and with known indicators of compromise.
In this blog post, we explored how Chrome Browser Cloud Management and Google Chronicle can be integrated to boost your security visibility. We highlighted the advantages of adopting Chrome Enterprise such as central management and visibility across operating systems, user management, control over extensions, and reporting. Following that, we guided through the steps to set up the integration between Chrome Enterprise and Google Chronicle. In our next blog post, we will show some examples of how Chrome event data can be used to create rules and investigate security incidents.

 Twitter
Twitter