- Google Cloud
- Cloud Forums
- ⚡Cloud Hub
- Recent changes?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
From what i see some folks are experiencing with issues while creating keys for service accounts even being Admin/Owner. Same problem. The interesting thing that i was able to do it even a month ago (I'm an Owner). Now creation key policy is disabled. Did i miss this annonsment or update? Could someone share it? Thank you in advance
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @zinger ,
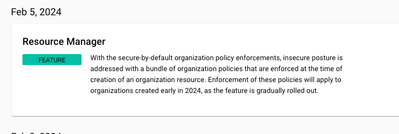
Welcome on the Google Cloud Community. I've found entry in release notes saying something about secure-by-default org policy enforcement around Feb 5 2024
I've search for secure-by-default phrase and got this: https://cloud.google.com/resource-manager/docs/secure-by-default-organizations#:~:text=The%20secure%....
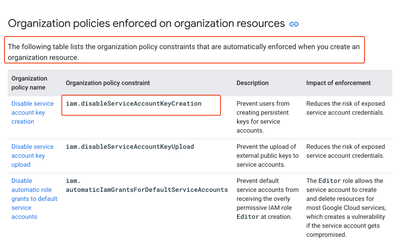
So it looks like Google have a enforcement action for all organizations at this moment, which enabling SA keys creation. I think it's becuase SA keys without proper policy of keys rotation are against security best practices ( WIF is more secured in this matter).
cheers,
DamianS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello, Damian and thank you for quick reply!
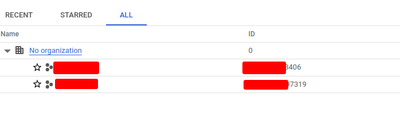
Now it's getting even more confusing: turned out i have no organization at all. Does it mean i have to create it first and as a super admin change policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's quite confusing also for me. You can't assign org policies without having org in place. However it looks like those Org policies are set by default to enforce. Let me ask, did you've been invited to those project by anybody else, or you just using your billing card, and without any org dealing with cloud ?
cheers,
DamianS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Additionally I've created issue ticket regarding this: https://issuetracker.google.com/issues/335695517
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i've been invited, you're right. the point is that even the project owner can't disable this policy (lack of permissions). thank you for your help, keeping an eye on the ticket
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically to deal with Org Policies you must have
roles/orgpolicy.policyAdminassigned to your IAM user. So even if you are Org Admin, which have more permissions than Project Admin or ( Owner ) you will not be able to deal with policies. If the person who invited you, is able to grant
roles/orgpolicy.policyAdmin and then make an exception based on tag to your project, SA keys creation functionality will be restored. But if you don't want to utilize keys anymore due to security reason, highly recommend to use Workload Identity Federations instead of service keys.
Grab the cli command to grant mentioned role
gcloud organizations add-iam-policy-binding YOUR_ORG_ID --member='user:YOUR_EMAIL' --role='roles/orgpolicy.policyAdmin'- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For some reason the person who's invited me can't assign OrgAdm role to me:
Now i'm trying to move this project (under "No organization") to existing org, which is another journey. So far no luck..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
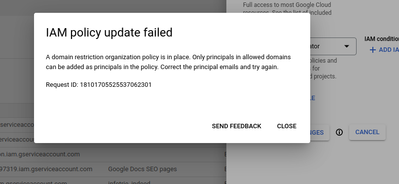
Hi,
yep. This error means, that only principals in trusted polices can be added to IAM. So, you must check which domains are whitelisted at policy constraint and add principal with that policy or add domain where your user has been created like @example.com or @company2.com and then you will be able to be added.
-
0auth2.0
1 -
ABAP SDK
1 -
access
2 -
accesstoken
1 -
Account
3 -
adf
1 -
Administrator
1 -
Advice
1 -
AI & Machine Learning
5 -
AI ML General
4 -
Analytics General
4 -
android
1 -
Android Management API
1 -
Apache Beam
1 -
API
29 -
API Gateway
5 -
API Key
4 -
API Security
1 -
API Verification
3 -
Apigee
2 -
Apigee General
2 -
App Dev General
1 -
App Development
1 -
App Engine
3 -
Appeals
1 -
archive
1 -
Artifact Registry
4 -
attemptResponseLog
1 -
attempts
1 -
Authentication
2 -
authorization code
1 -
Automation
1 -
AWS
1 -
basics
1 -
Batch
3 -
beginer
1 -
Best Practices
2 -
Beyond Corp Enterprise
1 -
Bi
1 -
BigQuery
14 -
Bill
1 -
Billing
95 -
billing account
9 -
bot
1 -
buckets
2 -
Bug
1 -
Business Intelligence
2 -
Career Development
1 -
Certification
2 -
Certification Announcements
1 -
CLI
2 -
Cloud
14 -
Cloud Build
5 -
Cloud Code
5 -
Cloud community
1 -
Cloud Composer
1 -
cloud console
2 -
Cloud cost management
1 -
Cloud DataFlow
1 -
Cloud Developer
2 -
Cloud Digital Leader
2 -
Cloud DNS
2 -
Cloud Endpoint
1 -
Cloud Error Reporting
6 -
Cloud Firewall
1 -
cloud function
1 -
Cloud Functions
1 -
Cloud Identity
2 -
Cloud Logging
1 -
Cloud Monitoring
4 -
Cloud Natural Language API
2 -
Cloud News
1 -
Cloud Profiler
2 -
Cloud PubSub
1 -
Cloud Run
5 -
Cloud SDK
3 -
Cloud Source Repositories
2 -
Cloud SQL for MySQL
2 -
Cloud SQL for Postgres
2 -
Cloud Storage
9 -
cloud tasks
2 -
Cloud Trace
1 -
Cloud VPN
1 -
Cloud Workstations
2 -
Cloud-native
1 -
clusters
1 -
Colab
1 -
Commercial
1 -
commitment used discount
1 -
Community
2 -
Community Challenges
2 -
Comply with domain verification
1 -
Compute
3 -
Compute Engine
8 -
Connectivity
1 -
Console
4 -
Container Registry
3 -
contains active resources
1 -
contract
1 -
copyright
1 -
Cost Optimization
3 -
country
1 -
Credits
2 -
cud
1 -
Customize Email Template
1 -
Dask
1 -
Data
1 -
Data Analytics
4 -
Data Catalog
1 -
Data Engineer
1 -
Data Transfer
1 -
Database
3 -
Database Migration Service
1 -
Datamesh
1 -
Dataplex
1 -
Dataproc
1 -
Datastream
1 -
delete
1 -
deleted
2 -
deleting Google workspace account
1 -
Developer Portal
1 -
Devices
1 -
Dialogflow
2 -
Digital Badging
1 -
display
1 -
DLP
1 -
document creation
1 -
Documentation
6 -
domain
2 -
doubleclickbidmanager
2 -
DR
1 -
Drive
2 -
dv360
1 -
Email Logs
1 -
emails
1 -
EMM
1 -
error
4 -
etc.
1 -
Events
3 -
expiration
2 -
Feedback
1 -
filter
1 -
firebase
8 -
firebase hosting
2 -
Firestore
4 -
flask
1 -
Free tier
6 -
Fundamental
2 -
gcloud
1 -
GCP
42 -
GCP Billing Account
20 -
GCP Billing Acount
5 -
gcp co
1 -
GCP Console
17 -
GCP Homepage url
1 -
GCP Project
3 -
gcs
1 -
General Discussion
44 -
General Miscellaneous
1 -
Geocoding
2 -
Geographic
1 -
GKE
4 -
GKE Enterprise
1 -
Gmail
2 -
Google API
3 -
Google App Engine
4 -
Google App Script
1 -
Google Chat
1 -
google cloud
2 -
Google Cloud Arcade Swag
1 -
Google Cloud Deploy
5 -
Google Cloud Function
1 -
Google Cloud Next
3 -
google cloud oauth
1 -
Google Cloud Platform
29 -
Google Cloud signup
2 -
google cloud verifaction
2 -
Google Console
4 -
Google Experts
1 -
Google Forms API
1 -
Google Identity Platform
4 -
Google Kubernetes Engine (GKE)
1 -
Google Maps
5 -
google sheet
1 -
Google Sheets
2 -
Google Sign-In
1 -
google street view
1 -
Google Translate
1 -
google vision
1 -
google workspace
4 -
Google Workspace Marketplace
3 -
google-app-engine
1 -
google-cloud-platform
1 -
Google_Client
1 -
googlecommunity
4 -
grpc
2 -
gsc
1 -
guarantees
1 -
guest attributes
1 -
homegraph
1 -
IAM
4 -
iam access
2 -
iap
1 -
Ideas
1 -
Identify
1 -
Identity & Access Management
7 -
Infrastructure as Code
2 -
Infrastructure General
2 -
Innovators
2 -
Innovators Help
11 -
Integration
1 -
Internet of Things
1 -
Introduction
20 -
Introductions
27 -
IoT
3 -
IoTCore
3 -
ip
1 -
issues
1 -
jarvis
1 -
JWT
2 -
Kafka
1 -
labels
3 -
Labs Support & Troubleshooting
2 -
Learning
2 -
Legacy
1 -
licence
1 -
liens
1 -
liens delete
1 -
limitations
1 -
List API
1 -
llo
1 -
load balancer
2 -
Location intelligence
1 -
logging logs
2 -
Login
1 -
Low-code
1 -
Managed Service for Prometheus
1 -
Mapping
1 -
Marketplace
4 -
me-central2
1 -
memorystore
1 -
Memorystore for Memcached
1 -
Memorystore for Redis
1 -
MERN Stack
1 -
metadata
2 -
Migration
4 -
MQTT
2 -
Myself
1 -
need to
2 -
Networking
3 -
New idea
1 -
News & Events
6 -
nginx
1 -
node.js
2 -
oauth
18 -
OAuth API verification
11 -
oauth app verification
1 -
oauth consent screen
14 -
oauth verifaction
1 -
oauth verifaction request
1 -
OCR
1 -
odoo
1 -
Oh
1 -
Open Source
5 -
Organization
5 -
Other
1 -
P1 Bug
1 -
pakdeslot
1 -
payment
3 -
Payments
1 -
Payments Profile
1 -
PCA
1 -
PCF
1 -
pdf
1 -
people
1 -
Perspective API
1 -
Phishing
1 -
pricing
3 -
Private Service Connection
1 -
Product Availability
1 -
Professional
1 -
Professional Collaboration Engineer
1 -
project
2 -
project delete
2 -
Projects
9 -
Promotion Codes
1 -
python
6 -
Quotas
3 -
rails
1 -
RDP
1 -
React Js
1 -
recovery
1 -
redirect_uri_mismatch
1 -
Redis
1 -
refresh token
2 -
refreshtoken
1 -
registration error
1 -
Research
1 -
response
1 -
restore billing account
1 -
results
1 -
retail
2 -
Retail API
1 -
retries
1 -
rickroll
1 -
ripple
1 -
roles
1 -
ruby
1 -
rust
1 -
SaaS
1 -
saml
1 -
Scheduler
1 -
Scopes Approval
1 -
screenshot
1 -
Search
3 -
Security
2 -
security and guarantees
1 -
Security Command Center
2 -
Security Keys
3 -
sending
1 -
Sensitive scope verification
1 -
Serverless
1 -
Service Account
3 -
Service Directory
1 -
session
1 -
setting
1 -
setup
1 -
Shared VPC
1 -
Signup Error
1 -
Similar items
1 -
SLA
1 -
slot gacor
1 -
slot gacor hari ini
1 -
sports
1 -
Sportsradar API
1 -
Spring Boot
1 -
static
2 -
static website
3 -
Status
1 -
Storage
3 -
storage class
1 -
Subject Matter Experts
2 -
subscription
1 -
Success Stories
1 -
Support
2 -
Support Team
1 -
survey
1 -
Suspension
1 -
system-gsuite
1 -
task
2 -
Tasks
1 -
terminal
2 -
Terraform
1 -
text detection
1 -
Tips & Tricks
10 -
token
1 -
traffic director
1 -
Training
3 -
translation hub
1 -
translator
1 -
trust and safety team
9 -
UEFI
1 -
unable
1 -
unknown
1 -
unkown
1 -
Unverified
1 -
Urgent
1 -
Use Cases
7 -
USFL
1 -
verification
3 -
Verify App
1 -
Vertex AI Platform
2 -
Vertex AI Workbench
1 -
Vision AI
1 -
VM
3 -
VPC
1 -
webpage
2 -
WebRisk
1 -
website
6 -
website cannot be reached
1 -
website offline
1 -
wgapp-cto
1 -
wif
1 -
wordpress
4 -
Workflows
2 -
Workload Manager
1
- « Previous
- Next »
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter