- Google Cloud
- Articles & Information
- Cloud Product Articles
- Workload Identity Federation - AWS to GCP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Workload Identity Federation (WIF)
Use WIF to connect AWS resources with GCP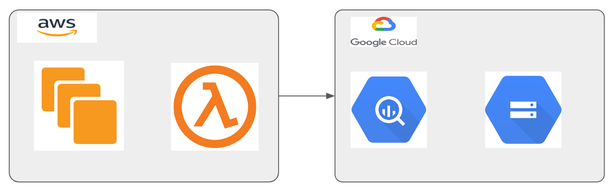
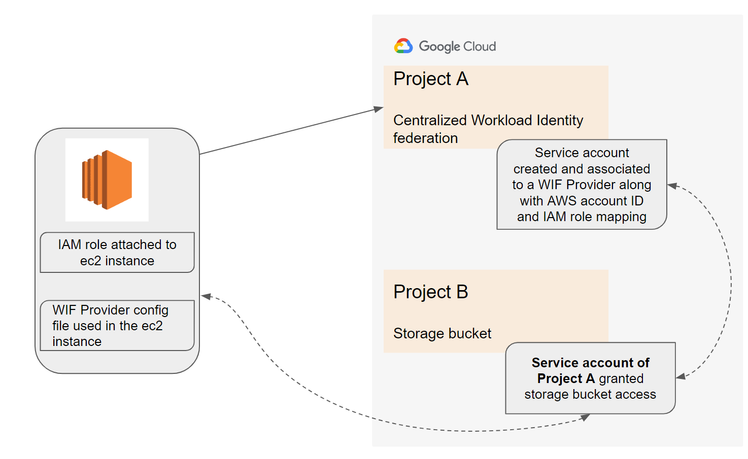
- Each ec2 instance in aws may have different iam role binding attached to them for providing access parameters to access services within aws. For it to access a GCP resource for eg: storage bucket it needs access parameters and in this case it will be passed via sts(session token service), WIF reads through the configuration and allows the resource to be accessed.
WIF Implementation:
- Enable APi’s- IAM, Resource Manager, Service Account Credentials, and Security Token Service APIs
- Roles
- Workload identity provider (admin)
- Organization admin
Org Policy modification
- Add the AWS account ID to further isolate to the AWS account from where the access request gets initiated
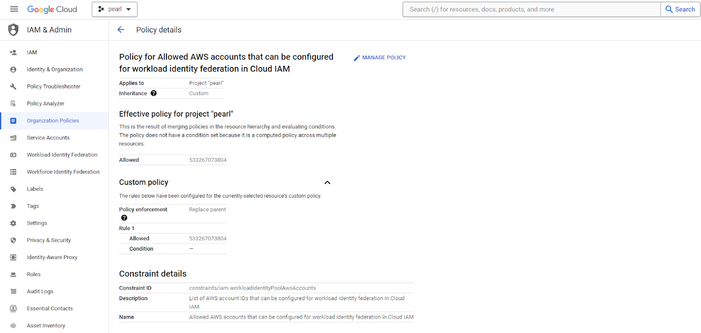
Add “https://sts.amazonaws.com”in the policy
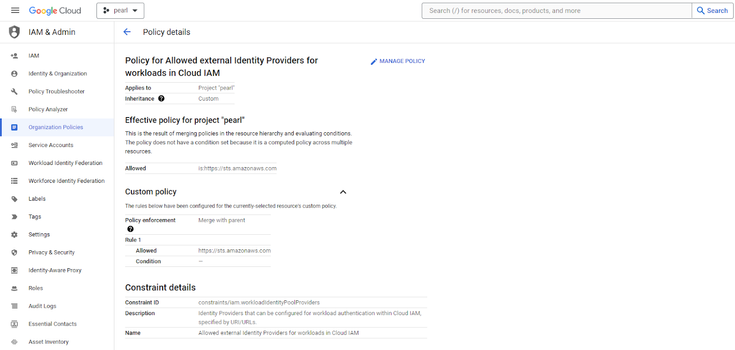
- Navigate to IAM & Admin under Pinned products and click on “Workload Identity Federation”
- It will launch the below Get started window
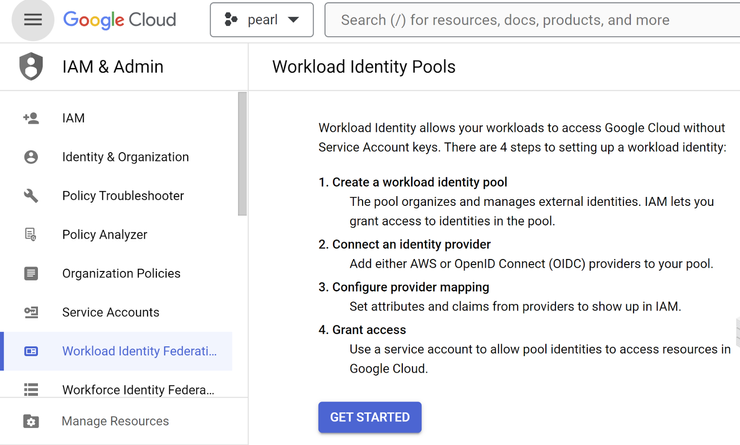
- Click on GET STARTED
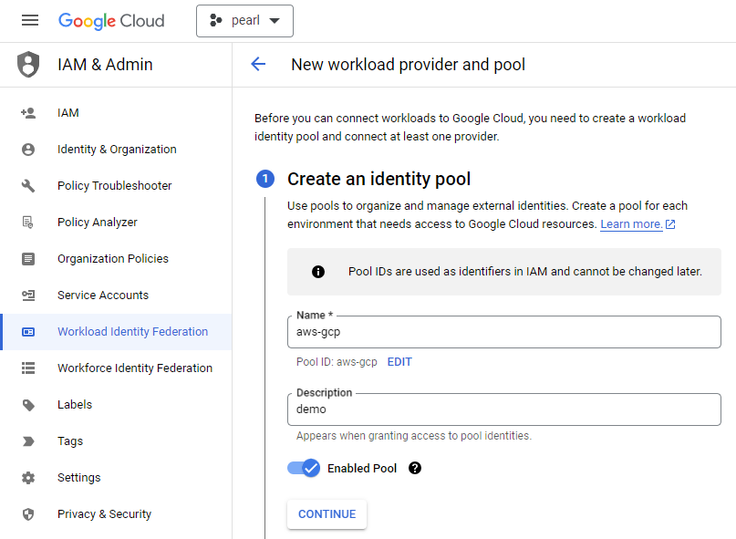
- Provide details for creating an Identity pool and click on continue
- Select AWS as the provider in the next stage for further configuring the workload identity pool
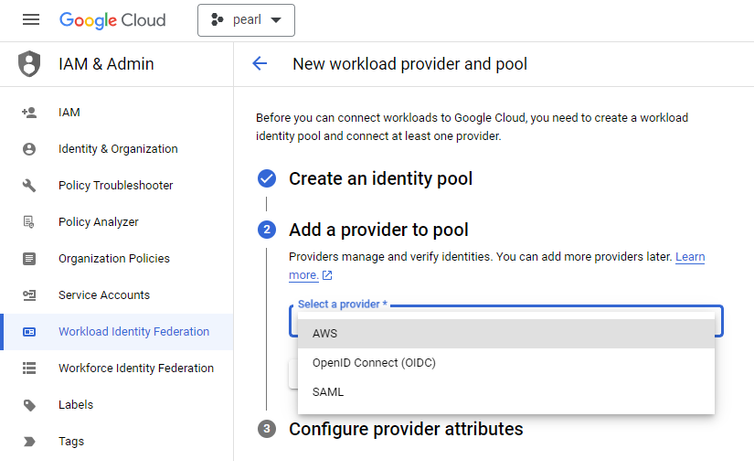
- After choosing AWS as the provider, add more details in individual tabs as below
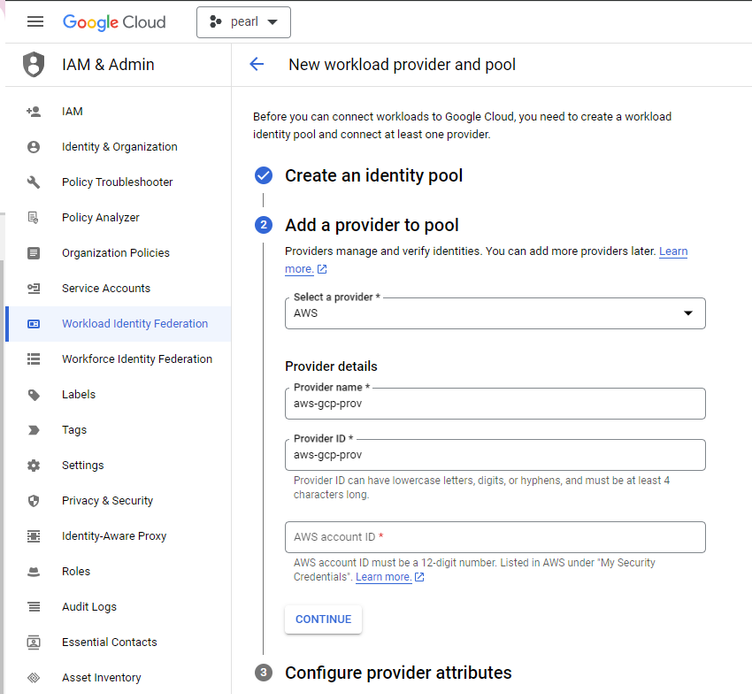
- In the AWS account ID section, add the respective AWS Account ID for enabling WIF. Once the configuration is saved and applied the WIF(provider pool) gets created
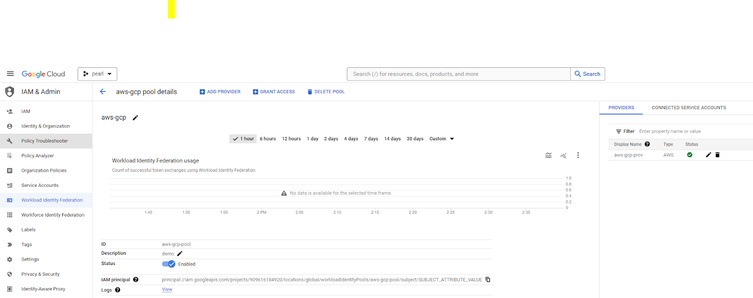
For AWS ec2 or lambda to access a GCS bucket hosted on GCP we need to create a service account in GCP without having the service account key generated.
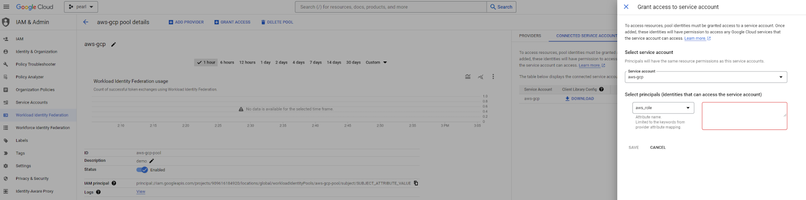
Click on the “grant access” and select the service account that you want to configure which will be used in the WIF for providing access to the AWS resource that will access on GCP environment / project
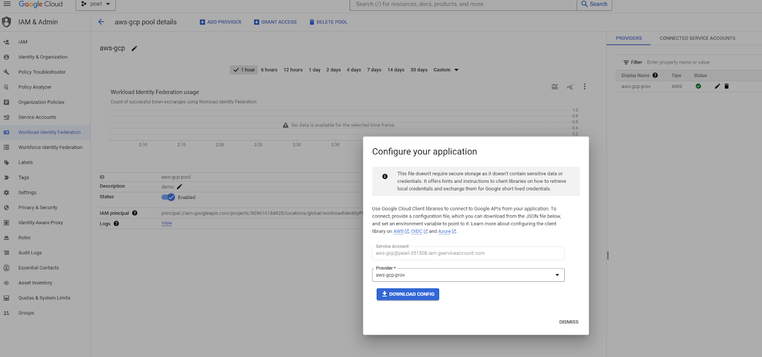
- Download the Client Library Config json file which will be later used to reference in the ec2 instance that will need to access GCP resources.
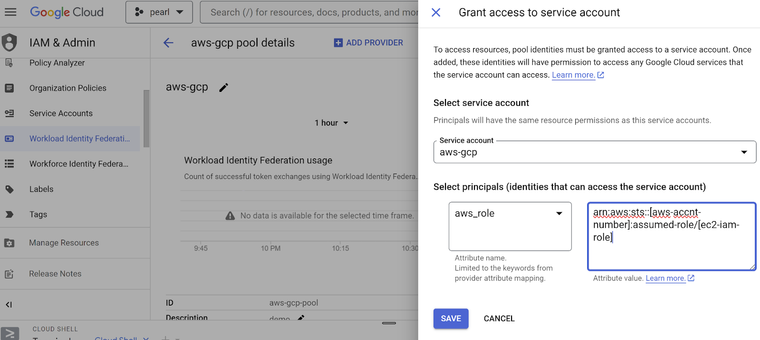
Prerequisites on AWS side:
- Create / deploy ec2 instance with an IAM role attached
Prerequisites on GCP side:
- Ensure
- arn:aws:sts::[aws-account-number]:assumed-role/[ec2-iam-role] is associated in the mapping of aws-role of the WIF provider
- Download the file
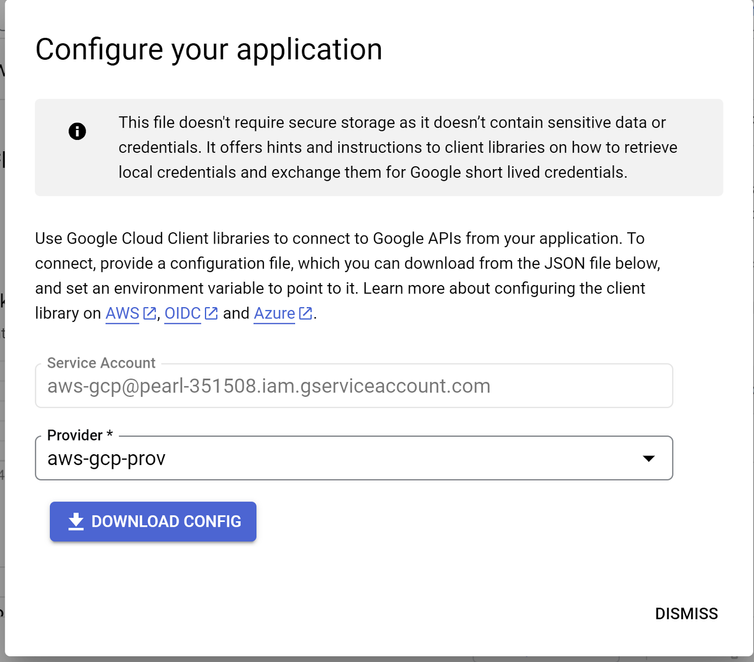
- Login to the ec2 instance copy this config file over to it and associate to the application or script which uses this config file to access the GCP resource over WIF.
References:
https://cloud.google.com/iam/docs/workload-identity-federation#why
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi! Thank you very much for this post
I followed the steps described here and read the documentation too for WIF.
I also implemented this in my lambda function: (only changing the url cause i'm listing projects)
https://github.com/googleapis/google-auth-library-nodejs?tab=readme-ov-file#using-external-identitie...
But I get this:
{"request":{"responseURL":"https://iamcredentials.googleapis.com/v1/projects/-/serviceAccounts/my-service-account-name@serviceaccount-id-gcp.iam.gserviceaccount.com:generateAccessToken"}},"status":403,"errors":[{"message":"Permission 'iam.serviceAccounts.getAccessToken' denied on resource (or it may not exist).","domain":"global","reason":"forbidden"}]}And my service account has the following permissions:
-Service Account Token Creator
-Viewer
-Workload Identity User
As I checked in the policy analyser, this permission iam.serviceAccounts.getAccessToken is granted for my service account
I hope you can help me. Thank you!

 Twitter
Twitter