- Google Cloud Security
- Community Blog
- Turn Intelligence into Action with Google Chronicl...
Turn Intelligence into Action with Google Chronicle Security Operations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
For years, organizations have struggled to operationalize threat intelligence to deliver security outcomes. Nearly every organization lacked the knowledge, skills and staff to source the right intelligence, correlate it with security telemetry, keep up with the changing threat landscape and reduce noise from false positives. The result? Underwhelming processes for threat detection, investigation and response, where threat intelligence is relegated mostly to enrichment of noisy security alerts.
Today, we are excited to announce the general availability of Applied Threat Intelligence in Google Chronicle Security Operations. Organizations can now uncover more threats with less effort. Our intelligence-driven security operations takes on the burden of operationalizing Google’s threat intelligence to unlock deeper threat hunting and investigation workflows, helping teams become 42% more efficient by providing high-quality insights about threats and enabling them to spend less time on monitoring activities.
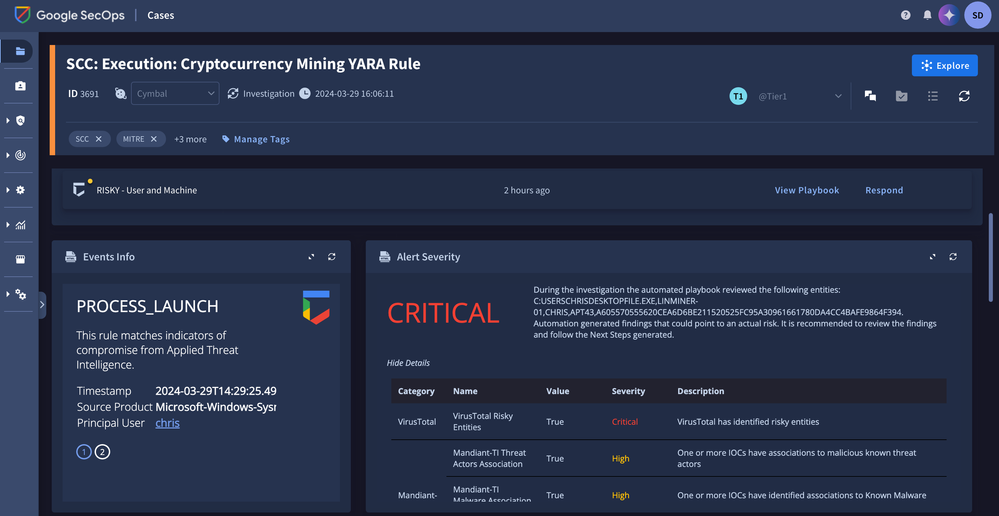
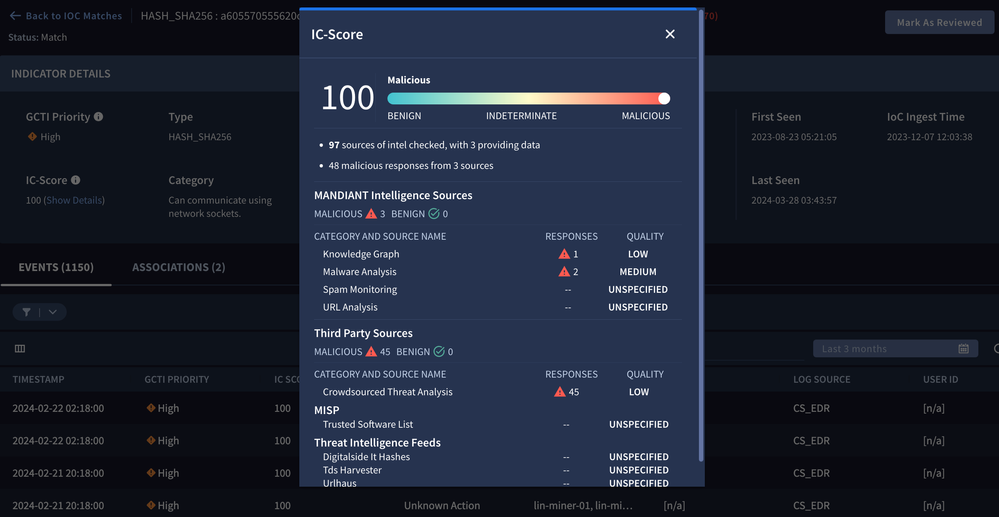
Applied Threat Intelligence in Google Chronicle Security Operations continuously analyzes twelve months of hot data against the wealth of Google’s threat intelligence, including the latest emerging threat intelligence from Mandiant’s incident response investigations. It automatically surfaces and prioritizes findings, complete with rich contextual information regarding threat actors and campaigns. Combined with curated detections developed by Google experts to address newly discovered threats, organizations can improve detection, investigation and threat-hunting workflows for better protection against the evolving threat landscape.
What’s different about our approach? Google provides broad and curated global threat visibility gleaned from protecting 5 billion devices running on Chrome, VirusTotal’s threat observatory that includes 6 billion URLs and 5 billion domains, and Mandiant’s frontline intelligence garnered from more than 1,000 security experts worldwide. But we don’t stop here. We take this intelligence and apply it to your unique environment to deliver the outcomes you need, making it possible to identify malicious activity operating in your environment and surface what you need to triage and respond to first in order to eradicate the threat. All without you having to manage the heavy lifting or complicated engineering.
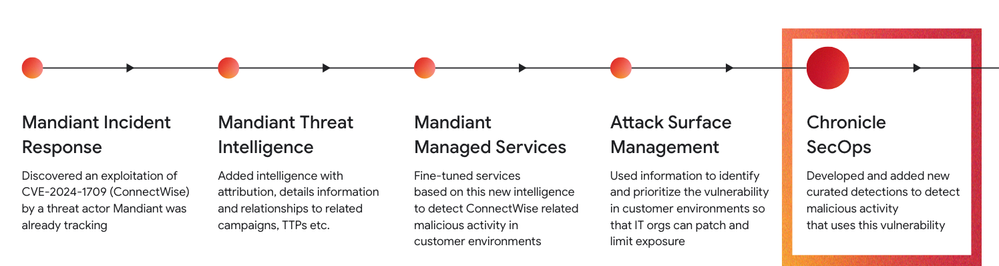
Google Chronicle Security Operations takes the burden off customers through a seamless chain of activity that converts intelligence gathered from active incident response engagements, combines that with additional information we have such as attribution, relationships with related campaigns, TTPs, etc., and turns that intelligence into curated detections that are specifically crafted by Google experts to address the latest emerging threats, and automatically delivers those new detections into the product.
“Google Chronicle Security Operations provides access to unique threat intelligence and advanced capabilities that are highly integrated into the platform. It enables security teams to surface the latest threats in a turnkey way that doesn’t require complicated engineering.” said Michelle Abraham, Research Director, IDC. ”Google is a potential partner for organizations in the fight against existing and emerging threats.”
Interested in seeing how intel-driven security operations can make a difference for you? If you’re attending Google Cloud Next, visit us on the show floor in the Security neighborhood or join our webinar on May 22, 2024 to learn more.

 Twitter
Twitter