- Google Workspace
- Workspace Forums
- Workspace Q&A
- Permissions for nested folders in a Shared Drive
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just found out that a shared drive cannot have permissions applied to folders nested within it.
This seems crazy. We have an HR folder that all of HR accesses and some folders only senior HR should have access to. I will request a feature but I have not been accepted into the group yet.
Other admins must have the same concerns. Google told me the solution to create another drive for 1 folder ? That will be impossible to administer.
Does anyone else have this concern or a solution?
Thanks!
- Labels:
-
Drive
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @joshgold21 :
This is indeed a question that comes up fairly frequently. Check out the discussion from a few months ago at https://www.googlecloudcommunity.com/gc/Workspace-Q-A/Granular-Graduated-Permissions-in-Shared-Drive... where it was discussed in a fair degree of detail.
Hope that helps, at least a little,
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks very much. I will try and figure a workaround but boy is it cumbersome. I was shocked that it could not be done. I thought I was just looking in the wrong place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Two years later and we are still dealing with this nonsense. I cannot believe they want to make an IDP/storage platform that can compete with Active Directory and still fail and simple permission fundamentals.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Waterfall" or "additive" permissions definitely take some getting used to. And Google is only one of many vendors adopting that model. Personally, I think they are actually a good bit more maintainable and secure, once you get your head around them.
As I mentioned above, this gets discussed here pretty frequently. See https://www.googlecloudcommunity.com/gc/Workspace-Q-A/Granular-Graduated-Permissions-in-Shared-Drive... for one of the more useful threads on that subject.
Hope that helps, at least a little,
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"I understand your concern regarding permissions on nested folders within a shared drive in Google Workspace. As of my last update in September 2021, Google Drive didn't allow direct permissions on nested folders within a shared drive. Permissions applied to the entire shared drive would affect all the folders and files within it.
Google often makes updates and improvements to its products, so it's possible that there have been changes or that new features are being developed to address this issue.
However, until a more direct solution is implemented, you might consider the following alternatives:
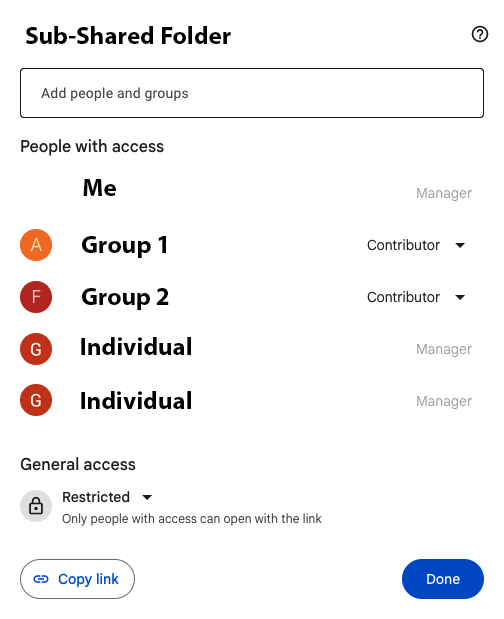
Create a sub-shared drive: An alternative is to create a sub-shared drive specifically for the folders that require different permissions. This way, you can apply distinct permissions to this sub-shared drive without affecting the rest of the shared drive.
Use permission groups: Instead of applying permissions directly to folders, you can create permission groups and add members to the groups with the appropriate permissions. Then, simply add these groups to the folders that need specific permissions.
Wait for updates or additional features: Regularly check Google Workspace updates, as new features may be added to improve permissions management in shared drives.
Contact support: If the current limitation is a significant obstacle to your needs, it's advisable to contact Google Workspace support and share your concerns. They can provide specific guidance and, in some cases, suggest temporary solutions.
Remember that the ability to manage permissions on nested folders may evolve over time as Google Workspace continues to be enhanced. Therefore, it's important to stay updated with the latest updates and features of the platform."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Michaelkildery wrote:Create a sub-shared drive: An alternative is to create a sub-shared drive specifically for the folders that require different permissions. This way, you can apply distinct permissions to this sub-shared drive without affecting the rest of the shared drive.
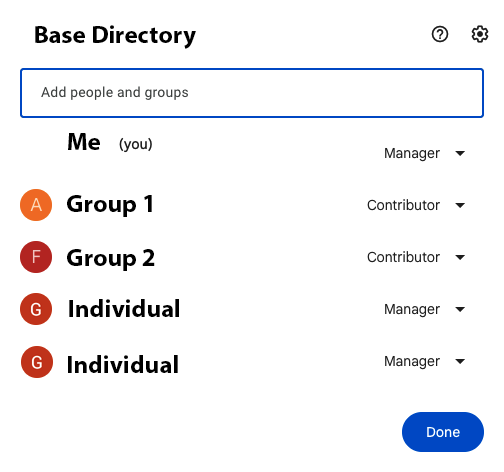
Can you explain in more detail what you mean by this? The way I would like to structure my folder structure is: Accounting and Finance > Accounting/Finance/Contracts/Et al. So I need everyone from Accounting and Finance to have access, but I only want the Accounting team to have access to the Accounting sub-folder within the Accounting and Finance Shared Drive. However, I have no way of removing the Finance group from the Accounting folder because it's inheriting permissions from the root Shared Drive directory.
I've included links to my Sharing settings to better explain my situation.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can do this, but the user experience isn't great.
Shared Drive "Accounting and Finance" - No users added (This is the essential piece, but also causes the bad user experience)
Sub-Folder "Accounting" - Users from Accounting added
Sub-Folder "Finance" - Users from Finance added
The problem arises in that using this method doesn't show the Shared Drive in the users' Google Drive. Instead they see only the folder that has been shared with them under "Shared with me." It would be better, I think, to show the Shared Drive for all users that have access in any capacity, but only show them the folders/files they actually have access to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
While "User experience" is a consideration - from an IT management perspective it must never - EVER - be at expense of security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Teligence I disagree. It should certainly be minimized and ideally seamless but a primary role of a modern IT administrators is to protect users from the bad guys and themselves.
We don't do these things to punish users, to make their lives difficult, or to slow down their work but many are necessary due to factors way outside the average persons control.
In any case, you CAN have permissions applied to folders under a shared drive. However, Google only supports an "additive" not a "subtractive" model. So you can make a folder available to extra people but you can't take them away.
We often use a shared drive such as for proposals with only managers having access to the main root drive. Then a folder is created and the proposal team is given access to that folder.
Perhaps this is helpful? -KAM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DATA that they have access to. Data management of trained, qualified,
vetted, responsible, and accountable users following approved procedures
can be given appropriate rights and any subsequent unauthorized access is
then restricted. IT admins can manage the way data is accessed, and in some
cases - even used, but IT admin CANNOT control the actions or intentions of
users.
-
2 step verification
1 -
Actions
1 -
Add-ons
13 -
Admin
1,219 -
Admin SDK
38 -
Administration
1 -
Adoption
1 -
Announcements
7 -
API Security
31 -
APIs
8 -
Apps Script
99 -
Auto Provisioning
12 -
Best Practices
1 -
Bug
1 -
Calendar
181 -
Card Framework
1 -
Change Management
2 -
Change Management & Adoption
1 -
Chat Apps
1 -
Classroom
63 -
Cloud Identity
74 -
Cloud SDK
1 -
Cloud Search & Intelligence
27 -
Contacts
62 -
Content
1 -
Copy
1 -
Currents
14 -
Customer & Partner Identities
23 -
Customer Support Portal
1 -
Delegated Administration
39 -
Device Management
93 -
Drive
554 -
Duet AI
6 -
Duplicate
1 -
Editors
83 -
Events
2 -
Feature Request
1 -
Finder
1 -
Forms
51 -
G Suite legacy free edition
14 -
G-Suite Legacy Snaffooo
1 -
GCDS
13 -
General Miscellaneous
1 -
Gmail
635 -
Google Chat
142 -
Google Credential Provider for Windows (GCPW)
55 -
Google Keep
1 -
Google Meet
131 -
Group Management
78 -
Groups
128 -
Hybrid Work
17 -
Improvement
1 -
Integrations
2 -
Introductions
87 -
Jamboard
5 -
Keep
6 -
Launches
1 -
Learning
1 -
locked
1 -
Mac
1 -
Marketplace
4 -
MDM
47 -
Migration
99 -
Mirror
1 -
Multi Factor Authentication
33 -
No-Low Code
1 -
Open Source
1 -
Other
113 -
Paste
1 -
Photos
28 -
Reduce AD dependence
6 -
Reporting
33 -
Scopes
6 -
Secure LDAP
14 -
Security
5 -
Security Keys
9 -
Shared Drive
197 -
Sites
59 -
Slides
1 -
Spaces
46 -
SSO
37 -
Stream
1 -
sync
1 -
Tasks
33 -
Tuesday Tips
18 -
User Security
100 -
Vault
33 -
Voice
72 -
Windows Management
27 -
Work Insights
14 -
Workflow
41 -
Workspace General
1,320 -
Workspace Marketplace
85
- « Previous
- Next »

 Twitter
Twitter