- Google Workspace
- Articles & Information
- Community Blogs
- How to set up Google Workspace Federation with Mic...
How to set up Google Workspace Federation with Microsoft Entra ID (Azure AD)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Juggling multiple logins for different platforms? Simplify your workflow! Connect Google Workspace with Microsoft Entra ID (previously Azure Active Directory) and empower users to access Google Workspace services with their familiar Entra ID credentials.
If your organization already utilizes Microsoft Entra ID for identity management, you can seamlessly extend its reach to Google Workspace. This allows users to log in to Google Workspace services with their existing Entra ID credentials, enabling a single sign-on experience.
This document provides information on configuring Entra ID as Identity Provider (IdP) for Google Workspace and also provides information on specific use case scenarios you may encounter during federation with Entra ID.
*This document assumes that users have already been provisioned from Entra ID to Google Workspace and exists both in Google Workspace and Entra ID.
- Single sign-on authentication flow with Microsoft Entra ID as IdP
- How to configure Microsoft Entra ID as IdP for Google Workspace
- Configuring Microsoft Entra ID
- Configuring Google Workspace for single sign-on
- Prevent additional prompts when using SSO with Entra ID
- How to configure:Adding links to the Microsoft My Apps portal
Single sign-on authentication flow with Microsoft Entra ID as IdP
Before we cover how to configure Microsoft Entra ID as the identity provider (IdP) for Google Workspace, let’s understand the sign-in flow.
The below diagram provides a high level authentication flow when a user tries to log in to Google Workspace using Microsoft EntraID as IdP.
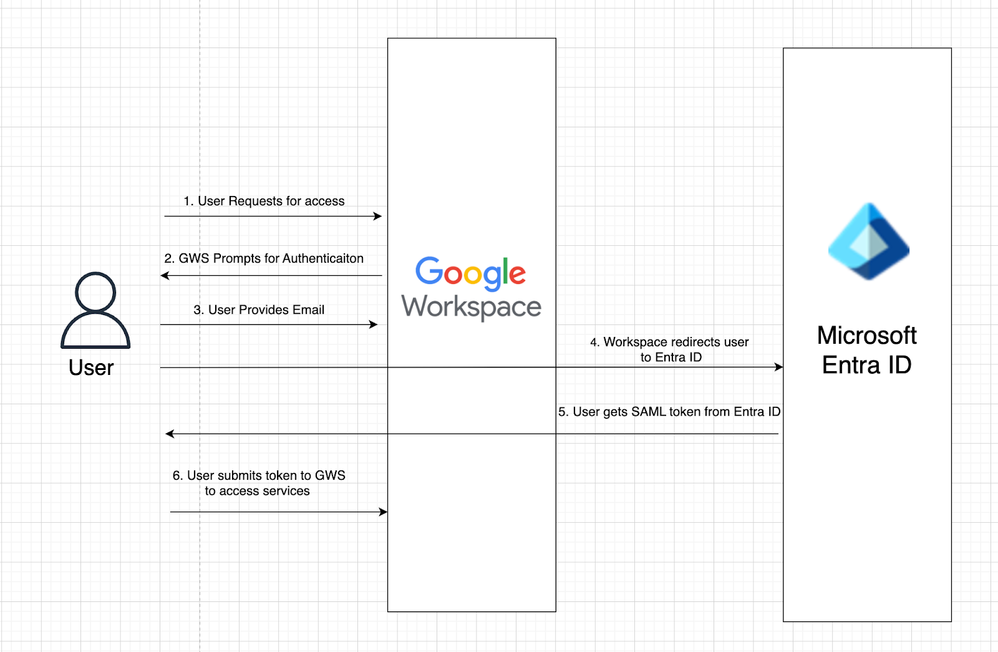
Below are the authentication steps as visualized in the diagram above:
- Step 1: User from domain - example.com requests for access to Google Workspace Services, by going to any of the Google Workspace service url (e.g. mail.google.com)
- Step 2: User is prompted for authentication by Google Workspace
- Step 3: User provides email address for authentication
- Step 4: Because the Google Workspace domain for example.com is configured to use Entra ID as the identity provider, Google redirects the user to Entra ID for authentication
- Step 5: User is redirected to Entra ID page and asked for their credentials. User provides the credentials and is authenticated by Entra ID. Entra ID provides a SAML token to the user.
- Step 6: User submits the SAML token to Google Workspace and is able to access services
How to configure Microsoft Entra ID as IdP for Google Workspace
You can configure identity federation with Entra ID by following these steps:
- Configuring Google Cloud/G Suite Connector by Microsoft in Entra ID - This step creates an application which is used to authenticate the user on Entra ID (IdP) and send the SAML token to Google Workspace.
- Configure Google Workspace to use Entra ID as identity provider.
Configuring Microsoft Entra ID
Create an enterprise application
- In the Azure portal, go to Microsoft Entra ID > Enterprise applications.
- Click New application.
- Search for Google Cloud, and then click Google Cloud/G Suite Connector by Microsoft in the result list.
- Set the name of the application to Google Cloud.
- Click Add. Adding the application may take a few seconds. You are then redirected to a page titled Google Cloud - Overview.
- In the menu on the left, click Manage > Properties.
- Set Enabled for users to sign-in to Yes.
- Set User assignment required to Yes unless you want to allow all users to use single sign-on.
- Click Save.
Configure user assignment
If you already know that only a certain subset of users need access to Google Cloud, you can optionally restrict the set of users to be allowed to sign in by assigning the enterprise app to specific users or groups of users.
If you set user assignment required to No before, then you can skip the following steps.
- In the menu on the left, click Manage > Users and groups.
- Click Add user.
- Select Users and groups/None Selected.
- Select the users or groups you want to allow single sign-on for.
- Click Select.
- Click Assign.
Configure SAML settings
Configure the below settings to enable Cloud Identity to use Microsoft Entra ID for authentication:
- In the menu on the left, click Manage > Single sign-on.
- On the ballot screen, click the SAML card.
- On the Basic SAML Configuration card, click Edit.
- In the Basic SAML Configuration dialog, enter the following settings:
- Identifier (Entity ID): google.com
- Reply URL: https://www.google.com/
- Sign on URL: https://www.google.com/a/PRIMARY_DOMAIN/ServiceLogin?continue=https://console.cloud.google.com/, replacing PRIMARY_DOMAIN with the primary domain name used by your Cloud Identity or Google Workspace account.
- Click Save, and then dismiss the dialog by clicking X.
- On the SAML Signing Certificate card, find the entry labeled Certificate (Base 64) and click Download to download the certificate to your local computer.
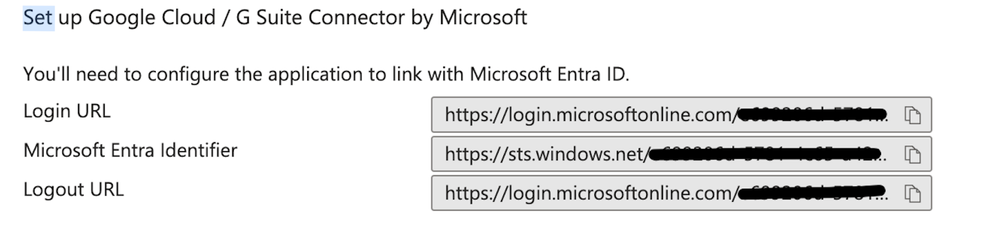
- On the Set up Google Cloud card, look for the Login URL. You need this URL shortly.
If you use multiple Identity providers and are using “SSO Profiles” to apply Identity Federation for an organizational unit (OU), the EntityID and ReplyURL are changed. You can get these details in the “Third Party SSO Profiles” section:
- Under Security —> Authentication → SSO With Third Party →Third Party SSO Profiles
- Click the SSO Profile if already created or Click “Add SAML Profile”
- Under SP Details, copy the “Entity ID” and ACS URL details. These are of the form below, where “xxxxxx” is a unique relying party identifier:
Entity ID : https://accounts.google.com/samlrp/metadata?rpid=xxxxxxx
ACS URL : https://accounts.google.com/samlrp/acs?rpid=xxxxxxx - Use the URLs identified in the above steps, while configuring the SAML setting in Entra ID.
The next steps differ depending on whether you map users by email address or by UPN (user principal name).
If you used UPN to map and provision users in Workspace:
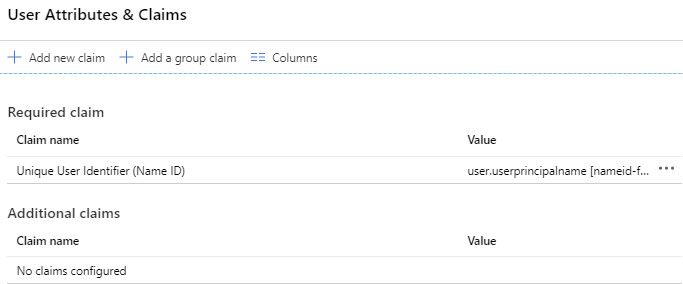
- On the Attributes & Claims card, click edit Edit.
- Delete all claims listed under Additional claims. You can delete records by clicking the … button and selecting Delete. The list of attributes and claims now looks like the following:
-
Dismiss the dialog by clicking X.
If you used Email to map and provision user in Workspace:
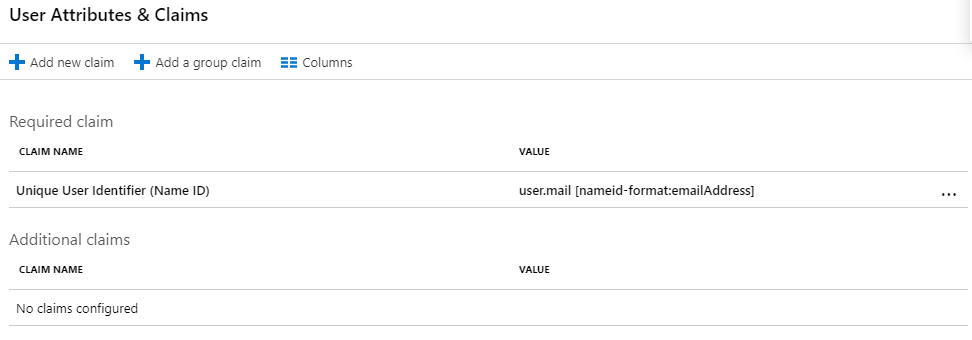
- On the User Attributes & Claims card, click edit Edit.
- Select the row labeled Unique User Identifier (Name ID).
- Change Source attribute to user.mail.
- Click Save.
- Delete all claims listed under Additional claims. To delete all records, click more_horiz, and then click Delete.
- Dismiss the dialog by clicking close
What if the Entra ID UPN domain suffix does not match the email domain in Google Workspace?
Consider the below scenario:
User has UPN (user principal name) in Entra ID: user@msdomain.com
User has primary email in Google Workspace: user@gwsdomain.com,
In such a scenario, if claims (UPN, email) are sent without changing from Entra ID to Google Workspace, Google Workspace would not identify the user user@msdomain.com, because the primary address for the user is different in Google Workspace.
Entra ID provides a method to send transformed claims to Google Workspace by substituting different domains. Use the steps below for transforming the claims in Entra ID:
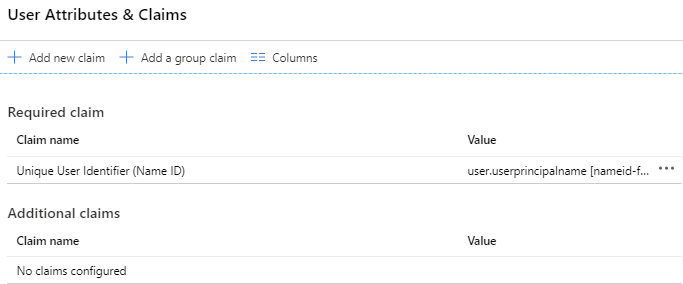
- On the User Attributes & Claims card, click edit Edit.
- Delete all claims listed under Additional claims. You can delete records by clicking the … button and selecting Delete.The list of attributes and claims now looks like the following:
- Click Unique User Identifier (Name ID) to change the claims mapping.
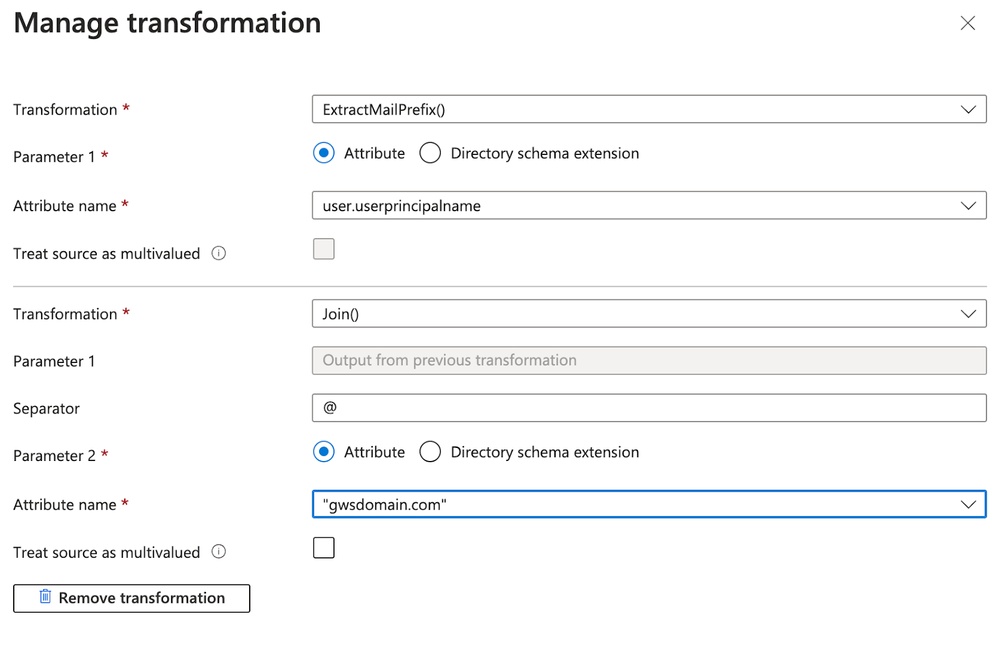
- Set Source to Transformation and configure the following transformation:
- Click Add.
- Click Save.
The first transformation, ExtractMailPrefix, extracts the prefix from the user's UPN and the second transformation joins it with the attribute name mentioned in Parameter 2 to create the email which would be sent to Google Workspace.
For example, user@msdomain.com would be converted to user@gwsdomain.com.
*Please note that, the above transformation assumes that the prefix in Entra ID UPN and Google Workspace primary email address are the same and only the domain is different. Also, when logging in to Entra ID, users need to provide the Entra ID UPN, which is different from the Google Workspace email address.
Configuring Google Workspace for single sign-on
Now that you've prepared Microsoft Entra ID for single sign-on, you can enable single sign-on in your Cloud Identity or Google Workspace account:
- Open the Admin Console and log in using a super-admin user.
- In the menu, click Show more and go to Security > Authentication > SSO with third-party IdP.
- Click Add SSO profile.
- Set Setup SSO with third party identity provider to enabled.
- Enter the following settings:
- Sign-in page URL: Enter the Microsoft Entra ID Login URL. The Login URL is on the Set up Google Cloud card in the Azure Portal under Configuration URLs > Login URL.
- Sign-out page URL: https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0
- Change password URL: https://account.activedirectory.windowsazure.com/changepassword.aspx
- Under Verification certificate, click Upload certificate, and then pick the token signing certificate that you downloaded previously.
- Click Save.
If you're using SSO Profile to enable Identity Federation for an OU, add the above URLs under SSO profile and assign the Profile to OU.
When configuring SSO Profile for OU, you would need EntityID for the Identity Provider. You can get this in the Application created in Entra ID.
- In the Azure portal, go to Microsoft Entra ID > Enterprise applications.
- Search for Google Cloud, and then click the application which was Created in previous steps.
- Click Single Sign-on and scroll down to the bottom.
- Microsoft Entra ID Identifier details are available in the section below:
Test by signing-in with a user. The user should get redirected to the Azure login page. Once authentication is successful, they should be able to access Google Workspace.
Prevent additional prompts when using SSO with Entra ID
While it is possible to have SSO enabled with Entra ID, it shows additional prompts when trying to access the service (i.e. after providing login details at Google login, Entra ID requests for the username again).
While it's not currently possible to completely bypass the second prompt, this can be addressed with a workaround by publishing Google Workspace apps in the MyApps portal in Entra ID with special URLs, available in this documentation: Microsoft My Apps portal integration | Cloud Architecture Center
These URLs send a login hint, which prevents additional prompts at Google side. The login hint provides extra information to Google Cloud Identity for silent authentication, eventually providing a seamless experience for the end user.
How to configure: Adding links to the Microsoft My Apps portal
- In the Azure portal, go to Microsoft Entra ID > Enterprise applications.
- Click New application.
- Click Create your own application and enter the following:
- The name of your app: Enter the name of the Google service as indicated in the preceding table.
- What are you looking to do with your application: Select Integrate any other application you don't find in the gallery (Non-gallery).
- Click Create.
- Select Properties.
- Change the logo to the file linked in the table.
- Click Save.
- In the menu on the left, select Single sign-on.
- Select Linked.
- Enter the URL for the specific service you wish to use this application for, from the list provided in this documentation.
- Assign the App to the user so it shows under MyApps for the user.
- Use the App for login directly from Azure
The sign-in operation will continue to be handled by the “Google Cloud Connector Application,” which was created in previous steps.
Hope this document gives you some more clarity on Identity Federation and helps in configuring Google Workspace Identity Federation with Entra ID.

 Twitter
Twitter