- Google Workspace
- Articles & Information
- Community Blogs
- Improve the security posture of your Google Worksp...
Improve the security posture of your Google Workspace environment: How to set up DNS records
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Why security matters
Even if your company has strong security controls in place, there is always room for improvements. There are trade-offs administrators need to consider when deciding between security for their organization and what technology and features their users want to access.
Each Google Workspace Administrator should have at least a basic understanding of service security concepts - to support the users and daily operations of the company.
This article will cover the importance of security and why it is essential for businesses. I will introduce you to DNS record types and how they help to protect your domain.
Before we jump into the technical aspects of Workspace configuration, let me introduce you to some dangers of the modern internet.
Whether it's staying compliant with the latest regulations or facing cyber threats a few weeks ago, every administrator might have different motivations to rethink their current security setup. The common point is that having strong policies in place helps you and your users to stay safe, and focus on what is really important in your work.
Keeping organizations secure is no easy task for any admin. These days, attackers are inventing new ways to trick the user. There are many ways of tricking the end-user, with some of the most popular as follows:
- Phishing emails - most of the attacks start with an email that your user might receive from someone that has an email address of your domain (or the one that looks exactly the same).
- Malware attachments - typically installed on the device, received with malicious email.
- Lack of control - employee negligence, extortion, and external threats, Admins have limited control over user emails.
- Data exfiltration - accidental or intentional sharing of corporate information outside the organization.
Out of the box Workspace services aim for balance of security and usability, that provides the best experience for the end-users.
It all starts with the DNS
Modern email services such as Gmail, by default apply security policies that secure the end user in the background. Depending on your company and its needs, these can be adjusted. There is a recommended bare minimum configuration that each administrator has to do to secure email communication - it’s DNS configuration.
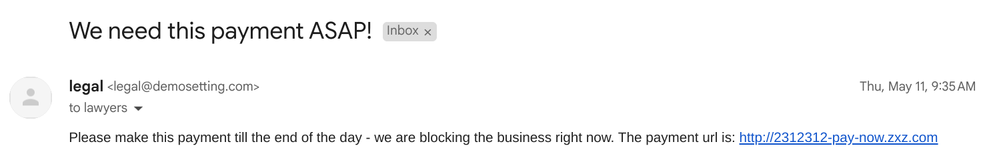
Have you ever wondered why this strange email reached out to your inbox? Even if it’s obvious spoofing, it might still trick some users! How can we make it harder for the attacker to pretend to be someone internal?
One of the email service misconfigurations that I see often in customers' environments is when the DNS records of the services are configured incorrectly or they are not in place at all.
Email applications, such as Gmail, are using domains to send messages - different mail protocols are communicating with the recipient servers, which can verify the current setup of our domain, and if we are authorized to send messages from it.
DNS records help with email security in multiple ways, including:
- Preventing email spoofing, which is when a sender's email address is pretending to be the address of someone within the organization.
- Blocking or quarantine phishing emails, which are emails that try to trick recipients into clicking on malicious links or attachments.
- Protecting against malware, malicious software that can be spread through email attachments.
- Enabling email authentication, which helps to verify the sender of an email and prevent email fraud.
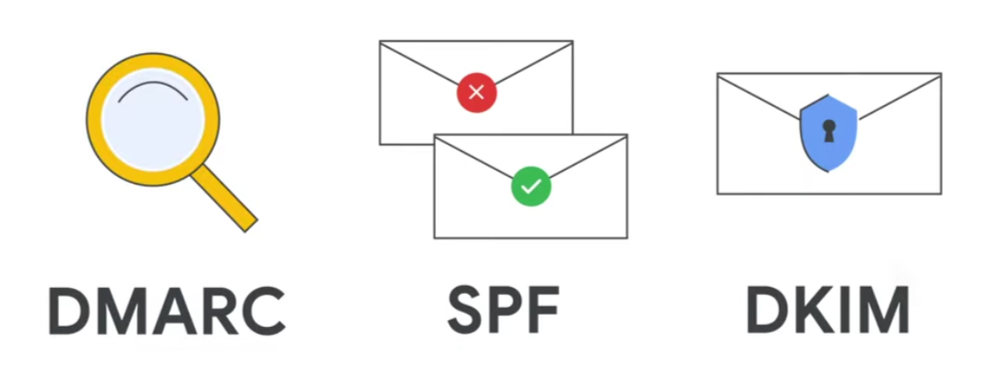
DNS record types that support Gmail security
You might want to set up the DNS of the domain when you deploy Google Workspace for the first time, or when you add a new domain to the account. Initial configuration should include the following records:
SPF Record (Sender Policy Framework)
The main purpose of the SPF record is to protect the domain from being spoofed (misused by the other servers), and prevent messages from being marked as spam. Many spam filters and mail servers by default use an algorithm to mark emails as wanted or unwanted, based on the SPF record values.
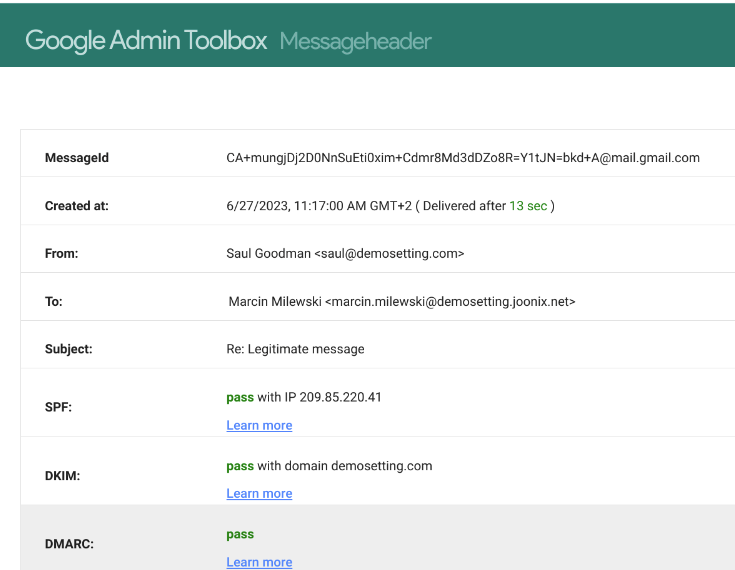
When SPF is configured correctly (holds a list of IP addresses and services with the chosen policy), the receiving server can check whether the email you send actually comes from you. In the case that the server from which you are sending is not on the list - your message will be classified as not authenticated (and it might be delivered into the SPAM folder of the recipient).
You can use tools such as Google Message Header Analyzer to verify the message headers (that includes the information about the authentication results).
Without the SPF record, hackers and other malicious users can impersonate your domain, making messages appear to come from your organization or domain. Messages from your domain are also more likely to be sent to spam.
SPF is one of the must have records within your DNS configuration. Even if you do not plan to send any messages from your domain, you should add an SPF record with a reject policy at least, to avoid spoofing attempts.
The instructions on how to correctly configure SPF records can be found in this Help Center Article.
DKIM (DomainKey Identified Mail)
DKIM is a standard email authentication method that adds a digital signature to outgoing messages. Receiving mail servers that get messages signed with DKIM can verify messages actually came from the sender, and not someone impersonating the sender, by comparing the key that has been used to sign the message with the key published in DNS of the domain.
DKIM also checks to make sure message contents aren’t changed after the message has been sent.
When receiving servers can verify messages are from you, your messages are less likely to be marked as spam - that’s another benefit of having this record in place. DKIM also helps receiving email servers to verify that messages are actually from the organization shown in the email.
We recommend you always set up SPF and DKIM to protect your organization’s email and to support future authentication requirements.
The instructions on how to correctly configure the DKIM record can be found in this Help Center Article.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC is the third of the email standards used to help prevent spoofing and phishing of your organization’s Gmail.
To benefit from DMARC, you first have to enable SPF and DKIM authentication.
DMARC tells receiving mail servers what to do when they get a message that appears to be from your organization, but doesn't pass authentication checks, or doesn’t meet the authentication requirements in your DMARC policy record. It also provides reporting capabilities that can be used to monitor and learn more about the sources that send emails for your organization (whether authorized or unauthorized).
The instructions on how to correctly configure the DMARC record can be found in this Help Center Article.
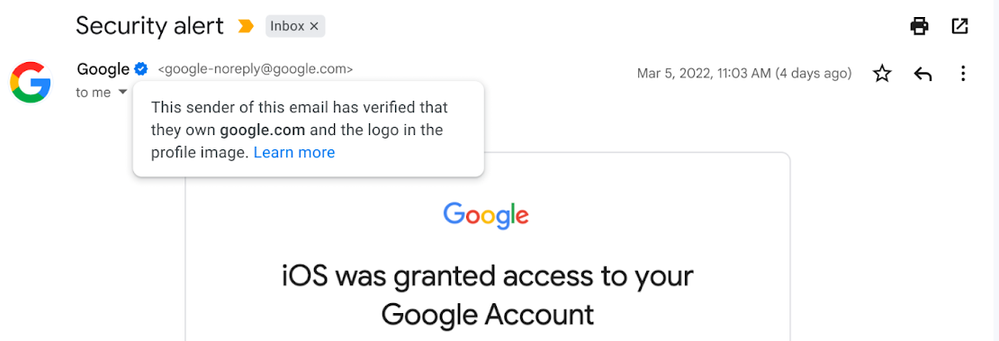
BIMI (Brand Indicators for Message Identification)
In addition to the above records, recommended for every organization, Google recently announced support for BIMI within Gmail, a feature that requires senders to use strong authentication and verify their brand logo in order to display a brand logo as an avatar in emails
If you want to additionally secure your communications in addition to all the DNS records described above, you can set up BIMI.
BIMI is an emerging email standard, it’s still being updated. Google tried to make the setup process as easy as possible, but some steps are technical.
Having DNS records that I described above for Google Workspace is important to ensure that your emails are delivered reliably and securely. It also helps to protect your domain from being used for phishing attacks.
In future articles we will explore different areas of security. We'll discuss basic and advanced security features, such as Gmail Safety, User security, Data loss prevention, and others, that will tighten the security of your environment.
Following this, you should get a good understanding of the security practices, and develop foundational knowledge that will help you with implementation within your company Google Workspace environment.
- Improve the security of your Google Workspace Environment: Protect users with BeyondCorp Enterprise
- Google Workspace Community Roundup: 2023 Year in Review!
- Leverage Google Meet to enhance connection and reduce your video conferencing spend
- How to set up Google Workspace Federation with Microsoft Entra ID (Azure AD)
- Save time and effort with Google Workspace Domain Transfer for Google to Google migrations

 Twitter
Twitter