- Google Cloud
- Cloud Forums
- ⚡Community Hub
- Re: Technology specific documentation on GKE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good Morning
I have Project starting to host Application on GKE .This is Private Cluster and all staff only (On-premise)facing connectivity Via Interconnect so no internet inbound or outbound. would like to check what all HA/DR and security aspects I should be go through other than IAM. Looking for Technical Infra specific documentation.
1. Documentation on Security for GKE (Pvt Standard Mode Cluster)
2. Infra documentation on Regional(Multi Zonal) GKE HA and DR like POD Replicas, Storage ,Failover, Load Balancers, I did not find single diagram showing GKE cluster with Nodes along with POD replicas in different zone and interface with downstream like Middleware and DB using LB ,Ingress,LB etc.
Please advice
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @avindia ,
Welcome to Google Cloud Community!
Here’s some HA/DR and security considerations for your private GKE Standard mode cluster connected via Interconnect.
- Security for Private GKE Standard Mode Clusters
Since you're operating a private cluster with no internet access, security is most important. Here's a layered approach, along with relevant documentation pointers:
- Network Security:
- VPC Network and Subnets: Properly segment your VPC. Dedicated subnets for your GKE nodes, services, and any associated infrastructure (like your jump host). Avoid overly permissive firewall rules.
- Firewall Rules: Implement strict ingress and egress firewall rules. Only allow necessary traffic. Think in terms of a "least privilege" network model. Specifically, for your on-premise connectivity via Interconnect:
- Allow ingress from your on-premise network's IP range to the GKE node IP range.
- Allow egress from the GKE node IP range to your on-premise network's IP range (if communication back to on-premise is needed).
- Consider using Service Accounts for Node Pools to further restrict outbound traffic.
- Private Service Access (PSA): This is critical for connecting to Google Cloud services (like Cloud SQL, Cloud Storage, etc.) without exposing them to the internet. Use PSA to establish a private network connection between your VPC and the Google service producer network. Allocate a dedicated IP range for PSA.
- Network Policy: GKE Network Policies are Kubernetes resources that control traffic between pods. Use them to isolate applications and services within the cluster.
- Cluster Security:
- Private Cluster Configuration: Ensure your GKE cluster is explicitly created as a private cluster (
--enable-private-nodesand--enable-private-endpoint). This prevents nodes from having public IP addresses. - Control Plane Access: Control how you access the Kubernetes API server (the control plane). You'll likely access it from your on-premise network. Authorize specific IP ranges from your on-premise network for API server access during cluster creation.
- Node Security:
- Shielded VMs: Consider using Shielded VMs for your node pools to protect against boot-level and kernel-level attacks.
- Container-Optimized OS (COS): COS is hardened and optimized for running containers, reducing the attack surface.
- Workload Identity: Use Workload Identity to allow your applications running in GKE to securely access Google Cloud services. Workload Identity binds Kubernetes service accounts to Google service accounts, eliminating the need to store and manage service account keys.
- Managed Certificate Authority Service (CAS): Consider using CAS to issue certificates for your services within the cluster. This simplifies certificate management and improves security.
- Image Security:
- Container Registry: Use Artifact Registry (or Container Registry) to store your container images. Scan your images for vulnerabilities during the build process.
- Binary Authorization: Implement Binary Authorization to ensure that only trusted images are deployed to your cluster.
- Application Security:
- Service Mesh (Istio): Consider implementing a service mesh like Istio for advanced traffic management, security (mTLS), and observability. This can greatly enhance your security posture.
- Best practices for GKE RBAC: Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
- Regional (Multi-Zonal) GKE HA and DR
Addressing the HA and DR aspects:
- Regional Clusters: Create a regional GKE cluster. This distributes the control plane and nodes across multiple zones within a region. This provides high availability if one zone fails.
- Node Pools: Create node pools that span multiple zones. GKE will automatically distribute nodes across those zones.
- Pod Replicas: Use Kubernetes Deployments or ReplicaSets to ensure you have multiple replicas of your pods running across different nodes (and therefore, ideally, different zones). Use
podAntiAffinityto strongly encourage pod replicas to be scheduled on different nodes and zones. Inter-pod affinity and anti-affinity can be even more useful when they are used with higher level collections such as ReplicaSets, StatefulSets, Deployments, etc. - Storage:
- Persistent Volumes (PVs) and Persistent Volume Claims (PVCs): Use Persistent Volumes (PVs) to provision storage. For regional HA, use regional persistent disks. These disks are replicated across multiple zones within the region. PVCs allow your pods to request storage from the PVs.
- Consider Cloud SQL or other managed databases: If you can, use Cloud SQL with its built-in HA and replication features. This simplifies your database management.
- Load Balancing and Ingress:
- Internal Load Balancer: Since you're private, you'll primarily use the Internal Load Balancer. Create a Kubernetes Service of type LoadBalancer. GKE will automatically provision an internal load balancer in your VPC. The internal load balancer distributes traffic to your pods across all nodes in the cluster, regardless of zone.
- Ingress: Use Ingress to expose your services to external (on-premise) clients. The Ingress controller will automatically configure the load balancer to route traffic based on the Ingress rules.
- Health Checks: The load balancer uses health checks to determine which pods are healthy and can receive traffic. Make sure your applications expose a health check endpoint.
- Failover:
- Automatic Failover: If a zone fails, GKE will automatically reschedule pods from the failed zone to healthy zones within the region. The load balancer will automatically stop sending traffic to the failed pods.
- Regional Persistent Disks: If you're using regional persistent disks, data will remain available even if one zone fails.
- DR Strategy (Beyond HA): HA within a region is different from Disaster Recovery. For DR, you'd need to replicate your cluster and data to a different region. This involves more complex setup using tools like Velero for cluster backup and restore, and cross-region replication for databases. Consider your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) when designing your DR strategy.
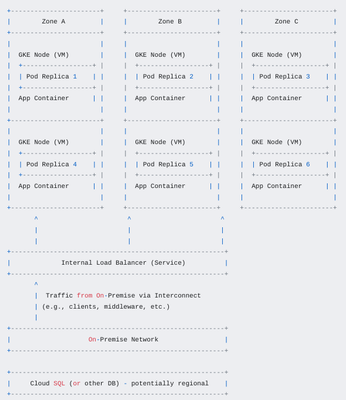
Conceptual Diagram
Explanation of the Diagram:
- Zones: The diagram shows three zones (A, B, and C) within a single Google Cloud region.
- GKE Nodes: GKE nodes (VMs) are distributed across the zones. These nodes are part of the regional GKE cluster's node pools.
- Pod Replicas: Pod replicas (instances of your application) are running on different nodes and, ideally, in different zones. The
podAntiAffinitysetting helps achieve this distribution. - Internal Load Balancer: A Kubernetes Service of type
LoadBalancercreates an internal load balancer. This load balancer distributes traffic across all healthy pod replicas, regardless of which zone they are in. The Internal LB allows On-Premise staff accessing Application/services.
- On-Premise Network: Your on-premise network is connected to your VPC via Interconnect. Traffic from on-premise clients flows through the Interconnect to the internal load balancer.
- Cloud SQL: The diagram also shows a connection to Cloud SQL. You would use Private Service Access for this connection.
Was this helpful? If so, please accept this answer as “Solution”. If you need additional assistance, reply here within 2 business days and I’ll be happy to help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the detailed response I Love this Google way !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @avindia ,
Welcome to Google Cloud Community!
Here’s some HA/DR and security considerations for your private GKE Standard mode cluster connected via Interconnect.
- Security for Private GKE Standard Mode Clusters
Since you're operating a private cluster with no internet access, security is most important. Here's a layered approach, along with relevant documentation pointers:
- Network Security:
- VPC Network and Subnets: Properly segment your VPC. Dedicated subnets for your GKE nodes, services, and any associated infrastructure (like your jump host). Avoid overly permissive firewall rules.
- Firewall Rules: Implement strict ingress and egress firewall rules. Only allow necessary traffic. Think in terms of a "least privilege" network model. Specifically, for your on-premise connectivity via Interconnect:
- Allow ingress from your on-premise network's IP range to the GKE node IP range.
- Allow egress from the GKE node IP range to your on-premise network's IP range (if communication back to on-premise is needed).
- Consider using Service Accounts for Node Pools to further restrict outbound traffic.
- Private Service Access (PSA): This is critical for connecting to Google Cloud services (like Cloud SQL, Cloud Storage, etc.) without exposing them to the internet. Use PSA to establish a private network connection between your VPC and the Google service producer network. Allocate a dedicated IP range for PSA.
- Network Policy: GKE Network Policies are Kubernetes resources that control traffic between pods. Use them to isolate applications and services within the cluster.
- Cluster Security:
- Private Cluster Configuration: Ensure your GKE cluster is explicitly created as a private cluster (
--enable-private-nodesand--enable-private-endpoint). This prevents nodes from having public IP addresses. - Control Plane Access: Control how you access the Kubernetes API server (the control plane). You'll likely access it from your on-premise network. Authorize specific IP ranges from your on-premise network for API server access during cluster creation.
- Node Security:
- Shielded VMs: Consider using Shielded VMs for your node pools to protect against boot-level and kernel-level attacks.
- Container-Optimized OS (COS): COS is hardened and optimized for running containers, reducing the attack surface.
- Workload Identity: Use Workload Identity to allow your applications running in GKE to securely access Google Cloud services. Workload Identity binds Kubernetes service accounts to Google service accounts, eliminating the need to store and manage service account keys.
- Managed Certificate Authority Service (CAS): Consider using CAS to issue certificates for your services within the cluster. This simplifies certificate management and improves security.
- Image Security:
- Container Registry: Use Artifact Registry (or Container Registry) to store your container images. Scan your images for vulnerabilities during the build process.
- Binary Authorization: Implement Binary Authorization to ensure that only trusted images are deployed to your cluster.
- Application Security:
- Service Mesh (Istio): Consider implementing a service mesh like Istio for advanced traffic management, security (mTLS), and observability. This can greatly enhance your security posture.
- Best practices for GKE RBAC: Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
- Regional (Multi-Zonal) GKE HA and DR
Addressing the HA and DR aspects:
- Regional Clusters: Create a regional GKE cluster. This distributes the control plane and nodes across multiple zones within a region. This provides high availability if one zone fails.
- Node Pools: Create node pools that span multiple zones. GKE will automatically distribute nodes across those zones.
- Pod Replicas: Use Kubernetes Deployments or ReplicaSets to ensure you have multiple replicas of your pods running across different nodes (and therefore, ideally, different zones). Use
podAntiAffinityto strongly encourage pod replicas to be scheduled on different nodes and zones. Inter-pod affinity and anti-affinity can be even more useful when they are used with higher level collections such as ReplicaSets, StatefulSets, Deployments, etc. - Storage:
- Persistent Volumes (PVs) and Persistent Volume Claims (PVCs): Use Persistent Volumes (PVs) to provision storage. For regional HA, use regional persistent disks. These disks are replicated across multiple zones within the region. PVCs allow your pods to request storage from the PVs.
- Consider Cloud SQL or other managed databases: If you can, use Cloud SQL with its built-in HA and replication features. This simplifies your database management.
- Load Balancing and Ingress:
- Internal Load Balancer: Since you're private, you'll primarily use the Internal Load Balancer. Create a Kubernetes Service of type LoadBalancer. GKE will automatically provision an internal load balancer in your VPC. The internal load balancer distributes traffic to your pods across all nodes in the cluster, regardless of zone.
- Ingress: Use Ingress to expose your services to external (on-premise) clients. The Ingress controller will automatically configure the load balancer to route traffic based on the Ingress rules.
- Health Checks: The load balancer uses health checks to determine which pods are healthy and can receive traffic. Make sure your applications expose a health check endpoint.
- Failover:
- Automatic Failover: If a zone fails, GKE will automatically reschedule pods from the failed zone to healthy zones within the region. The load balancer will automatically stop sending traffic to the failed pods.
- Regional Persistent Disks: If you're using regional persistent disks, data will remain available even if one zone fails.
- DR Strategy (Beyond HA): HA within a region is different from Disaster Recovery. For DR, you'd need to replicate your cluster and data to a different region. This involves more complex setup using tools like Velero for cluster backup and restore, and cross-region replication for databases. Consider your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) when designing your DR strategy.
Conceptual Diagram
Explanation of the Diagram:
- Zones: The diagram shows three zones (A, B, and C) within a single Google Cloud region.
- GKE Nodes: GKE nodes (VMs) are distributed across the zones. These nodes are part of the regional GKE cluster's node pools.
- Pod Replicas: Pod replicas (instances of your application) are running on different nodes and, ideally, in different zones. The
podAntiAffinitysetting helps achieve this distribution. - Internal Load Balancer: A Kubernetes Service of type
LoadBalancercreates an internal load balancer. This load balancer distributes traffic across all healthy pod replicas, regardless of which zone they are in. The Internal LB allows On-Premise staff accessing Application/services.
- On-Premise Network: Your on-premise network is connected to your VPC via Interconnect. Traffic from on-premise clients flows through the Interconnect to the internal load balancer.
- Cloud SQL: The diagram also shows a connection to Cloud SQL. You would use Private Service Access for this connection.
Was this helpful? If so, please accept this answer as “Solution”. If you need additional assistance, reply here within 2 business days and I’ll be happy to help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the detailed response I Love this Google way !
-
0auth2.0
1 -
ABAP SDK
1 -
access
2 -
accesstoken
1 -
Account
4 -
adf
1 -
Administrator
1 -
Advice
1 -
Agent
1 -
AI & Machine Learning
5 -
AI ML General
8 -
Analytics General
5 -
android
1 -
Android Management API
1 -
Announcements
1 -
Apache Beam
1 -
API
30 -
API Gateway
5 -
API Key
4 -
API Security
1 -
API Verification
3 -
Apigee
2 -
Apigee General
2 -
App Dev General
1 -
App Development
1 -
App Engine
3 -
Appeals
1 -
archive
1 -
Artifact Registry
4 -
Associate Cloud Engineer
1 -
attemptResponseLog
1 -
attempts
1 -
Authentication
2 -
authorization code
1 -
Automation
2 -
AWS
1 -
basics
1 -
Batch
3 -
beginer
1 -
Best Practices
2 -
Beyond Corp Enterprise
2 -
Bi
1 -
BigQuery
14 -
Bill
1 -
Billing
230 -
billing account
9 -
bot
1 -
buckets
2 -
Bug
3 -
Business Intelligence
2 -
Cant Update Console
1 -
Career Development
2 -
Certification
2 -
Certification Announcements
1 -
CLI
2 -
Cloud
14 -
Cloud Build
5 -
Cloud Code
5 -
Cloud community
1 -
Cloud Composer
1 -
cloud console
2 -
Cloud cost management
1 -
Cloud DataFlow
1 -
Cloud Deploy
6 -
Cloud Developer
2 -
Cloud Digital Leader
2 -
Cloud DLP
1 -
Cloud DNS
2 -
Cloud Endpoint
1 -
Cloud Error Reporting
10 -
Cloud Firewall
2 -
cloud function
1 -
Cloud Functions
1 -
Cloud Hero
1 -
Cloud Identity
2 -
Cloud Logging
5 -
Cloud Monitoring
4 -
Cloud Natural Language API
2 -
Cloud News
1 -
Cloud Profiler
3 -
Cloud PubSub
1 -
Cloud Run
5 -
Cloud SDK
3 -
Cloud Source Repositories
2 -
Cloud SQL for MySQL
3 -
Cloud SQL for Postgres
2 -
Cloud SQL for SQL Server
1 -
Cloud Storage
10 -
cloud tasks
2 -
Cloud Trace
1 -
Cloud Vision ApI
1 -
Cloud VPN
1 -
Cloud Workstations
2 -
Cloud-native
1 -
clusters
1 -
Colab
1 -
Commercial
1 -
commitment used discount
1 -
Community
2 -
Community Challenges
3 -
Comply with domain verification
1 -
Compute
3 -
Compute Engine
9 -
Connectivity
1 -
Console
4 -
Contact Center AI
1 -
Container Registry
3 -
contains active resources
1 -
contract
1 -
copyright
1 -
Cost Optimization
3 -
country
1 -
Credits
2 -
cud
1 -
Customize Email Template
1 -
Dask
1 -
Data
1 -
Data Analytics
4 -
Data Catalog
1 -
Data Engineer
1 -
Data Transfer
1 -
Database
3 -
Database Migration Service
1 -
Dataform
1 -
Datamesh
1 -
Dataplex
1 -
Dataproc
1 -
Datastream
2 -
delete
1 -
deleted
2 -
deleting Google workspace account
1 -
Developer Portal
1 -
Devices
1 -
Dialogflow
3 -
Digital Badging
1 -
display
1 -
DLP
1 -
document creation
1 -
Documentation
44 -
domain
2 -
doubleclickbidmanager
2 -
DR
1 -
Drive
2 -
Duplicate
1 -
dv360
1 -
Email Logs
1 -
emails
1 -
Embedding
1 -
EMM
1 -
error
5 -
etc.
1 -
Events
3 -
expiration
2 -
Feedback
1 -
Filestore
1 -
Filter
1 -
firebase
8 -
firebase hosting
2 -
Firestore
4 -
flask
1 -
Free tier
6 -
Fundamental
2 -
GCDS
1 -
gcloud
1 -
GCP
42 -
GCP Billing Account
20 -
GCP Billing Acount
5 -
gcp co
1 -
GCP Console
17 -
GCP Homepage url
1 -
GCP Project
3 -
gcs
1 -
Gemini
1 -
Gen App Builder
1 -
General Discussion
262 -
General Miscellaneous
3 -
Generative AI Studio
2 -
Geocoding
2 -
Geographic
1 -
GKE
6 -
GKE Enterprise
1 -
Gmail
2 -
google actions
1 -
Google AI Studio
2 -
Google API
3 -
Google App Engine
4 -
Google App Script
1 -
Google Chat
1 -
google cloud
2 -
Google Cloud Arcade Swag
1 -
Google Cloud Function
2 -
Google Cloud Next
3 -
google cloud oauth
1 -
Google Cloud Platform
29 -
google cloud project
1 -
Google Cloud signup
2 -
google cloud verifaction
2 -
Google Console
4 -
Google Experts
1 -
Google Forms API
1 -
google home
1 -
Google Identity Platform
5 -
Google Kubernetes Engine (GKE)
1 -
Google Maps
5 -
google sheet
1 -
Google Sheets
2 -
Google Sign-In
1 -
google street view
1 -
Google Translate
1 -
google vision
1 -
google workspace
4 -
Google Workspace Marketplace
3 -
google-app-engine
1 -
google-cloud-platform
1 -
Google_Client
1 -
googlecommunity
4 -
Groups
1 -
grpc
2 -
gsc
1 -
guarantees
1 -
guest attributes
1 -
homegraph
2 -
IAM
4 -
iam access
2 -
iap
1 -
Ideas
1 -
Identify
1 -
Identity & Access Management
9 -
Infrastructure as Code
2 -
Infrastructure General
3 -
Innovators
2 -
Innovators Help
52 -
Integration
1 -
Internet of Things
1 -
Introduction
20 -
Introductions
58 -
invalid
1 -
IoT
3 -
IoTCore
3 -
ip
1 -
issues
1 -
jarvis
1 -
JWT
2 -
Kafka
1 -
labels
3 -
Labs Support & Troubleshooting
4 -
Learn to Earn
4 -
Learning
2 -
Learning Logs Prompt
1 -
Legacy
1 -
licence
1 -
liens
1 -
liens delete
1 -
limitations
1 -
List API
1 -
llo
1 -
load balancer
2 -
Location intelligence
1 -
logging logs
2 -
Login
1 -
Low-code
1 -
Managed Service for Prometheus
1 -
Mapping
1 -
Marketplace
4 -
me-central2
1 -
memorystore
1 -
Memorystore for Memcached
1 -
Memorystore for Redis
1 -
MERN Stack
1 -
metadata
2 -
Migration
4 -
MQTT
2 -
Myself
1 -
need to
2 -
Networking
3 -
New idea
1 -
News & Events
19 -
nginx
1 -
node.js
2 -
oauth
19 -
OAuth API verification
11 -
oauth app verification
1 -
oauth consent screen
14 -
oauth verifaction
1 -
oauth verifaction request
1 -
OCR
1 -
odoo
1 -
Oh
1 -
Open Source
5 -
Organization
5 -
Other
3 -
P1 Bug
1 -
pakdeslot
1 -
partneradvantageportal
1 -
payment
3 -
Payments
1 -
Payments Profile
1 -
PCA
1 -
PCF
1 -
pdf
1 -
people
1 -
Perspective API
1 -
Phishing
1 -
pricing
3 -
Private Service Connection
1 -
Prizes & Swag
1 -
Product Availability
35 -
Professional
1 -
Professional Cloud Architect
1 -
Professional Cloud Developer
1 -
Professional Cloud Network Engineer
1 -
Professional Collaboration Engineer
1 -
Professional Data Engineer
1 -
project
2 -
project delete
2 -
Projects
9 -
Promotion Codes
1 -
python
6 -
Quotas
4 -
rails
1 -
RDP
1 -
React Js
1 -
Recommendations AI
1 -
recovery
1 -
redirect_uri_mismatch
1 -
Redis
1 -
refresh token
2 -
refreshtoken
1 -
registration error
1 -
Research
1 -
response
1 -
restore billing account
1 -
results
1 -
retail
2 -
Retail API
1 -
retries
1 -
rickroll
1 -
ripple
1 -
roles
1 -
ruby
1 -
rust
1 -
SaaS
1 -
saml
1 -
Scheduler
1 -
Scope
1 -
Scopes Approval
1 -
screenshot
1 -
Search
3 -
Security
2 -
security and guarantees
1 -
Security Command Center
2 -
Security Keys
3 -
sending
1 -
Sensitive scope verification
1 -
Serverless
1 -
Service Account
3 -
Service Directory
1 -
session
1 -
setting
1 -
setup
1 -
Shared VPC
1 -
Signup Error
1 -
Similar items
1 -
SLA
1 -
Speech-to-Text
1 -
sports
1 -
Sportsradar API
1 -
Spring Boot
1 -
static
2 -
static website
3 -
Status
1 -
Storage
3 -
storage class
1 -
Study Jam
1 -
Subject Matter Experts
3 -
subscription
1 -
Success Stories
9 -
Support
2 -
Support Team
1 -
survey
1 -
Suspension
1 -
system-gsuite
1 -
task
2 -
Tasks
1 -
Tensorflow Enterprise
1 -
terminal
2 -
Terraform
1 -
text detection
1 -
Tips & Tricks
61 -
token
1 -
traffic director
1 -
Training
3 -
Translation AI
1 -
translation hub
1 -
translator
1 -
trust and safety team
9 -
UEFI
1 -
unable
1 -
unexisting
1 -
unknown
1 -
unkown
1 -
Unverified
1 -
Urgent
1 -
Use Cases
52 -
USFL
1 -
verification
3 -
Verify App
1 -
Vertex AI Model Registry
1 -
Vertex AI Platform
3 -
Vertex AI Workbench
2 -
Video AI
1 -
Vision AI
2 -
VM
3 -
VPC
1 -
webpage
2 -
WebRisk
1 -
website
6 -
website cannot be reached
1 -
website offline
1 -
wgapp-cto
1 -
wif
1 -
wordpress
4 -
Workflows
2 -
Workload Manager
1 -
Workspace General
1
- « Previous
- Next »

 Twitter
Twitter