- Google Workspace
- Articles & Information
- Community Blogs
- Google Workspace and Office 365: Identity manageme...
Google Workspace and Office 365: Identity management during coexistence
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
As an IT Admin, when you’re migrating users from Office 365 to Google Workspace, you’ll face coexistence scenarios.
Coexistence is when a newly-deployed system lives side-by-side with one or more legacy systems. Coexistence comes with its own set of challenges, including identity management.
This article will focus on how to manage identities and keep Google Workspace (GW) and Office 365 (O365) users in sync, leveraging coexistence and identity features to achieve collaboration and cross functioning.
Current tech landscape
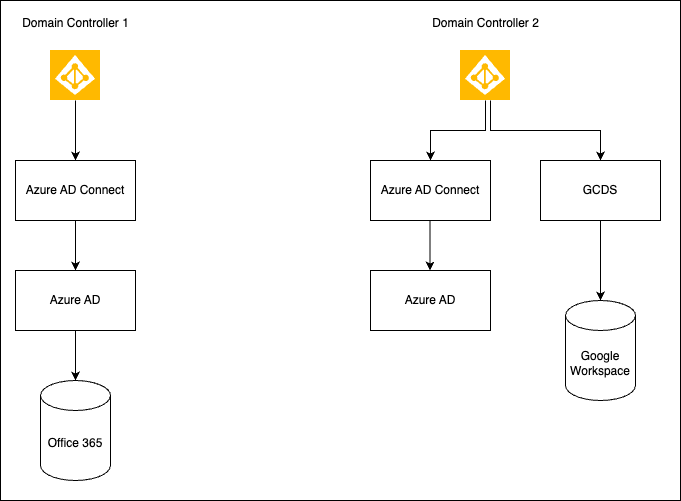
Let's say O365 users are on Domain Controller 1 and GW users are on Domain Controller 2, with separate domain names on both the Domain Controllers.
Objectives
-
Sync GW Directory contacts to O365 accounts - Requires setting up Mail enabled contacts / connect two Azure Active Directory (AD) tenants via FIM (Forefront Identity Manager) method.
-
O365 users can collaborate on Drive and Meet with GW users - Requires user provisioning via GCDS (Google Cloud Directory Sync) / G Suite connector and Password Sync via GSPS (G Suite Password Sync) or configure partial SSO for O365-backed Google accounts, keeping O365 as a IdP (Identity Provider).
-
Sync O365 Directory contacts to GW accounts - Requires setting up GCDS Shared contacts on Domain controller 1 with SA (Super Admin) of GW.
This article will focus more on Objectives 2 and 3.
Assumptions (to achieve Objectives 2 and 3)
- The Google Workspace instance is in a Partial Domain licensing scenario with multiple SKU(s)
- The Office 365 identity domain is registered as a secondary domain under the Google Workspace instance
- Cloud Identity Free edition is used to provision Google accounts for O365 users
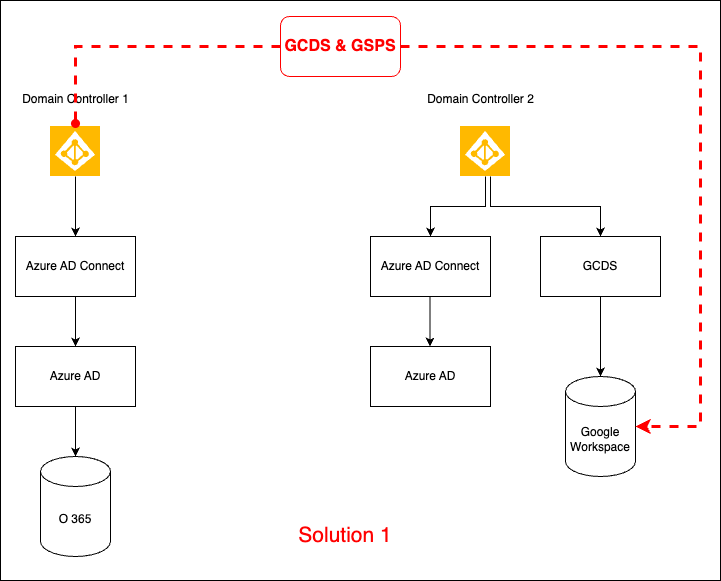
Solution 1: Create O365 users on Google Workspace using Google Cloud Directory Sync and G Suite Password Sync
- Authorize GCDS and GSPS on O365 Local Active Directory with Super Admin credentials of GW
- Map AD OU (Organization Unit) with GCDS and enabled licensing feature via security group. This will provision users directly to GW OU where auto licensing is OFF by default.
- At this stage, O365 user NOW has another account with similar naming convention, on a similar domain but a Google one
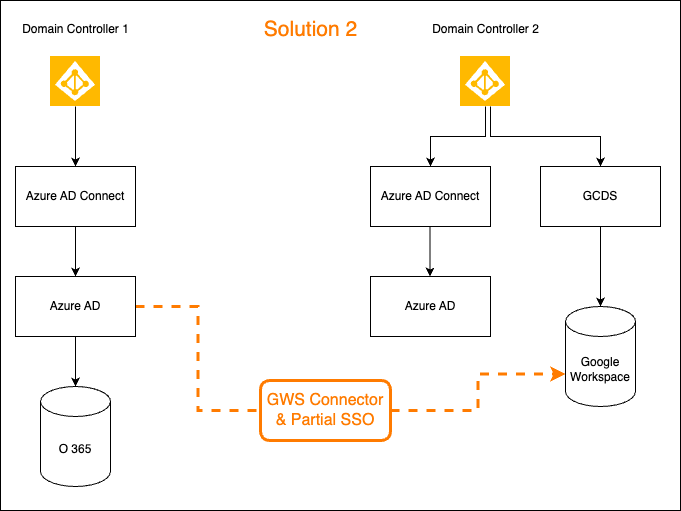
Solution 2: Federated Identity using G Suite Connector and Partial SSO from Google Workspace
- Authorize G Suite Connector on Azure AD with GW Super Admin
- Turn on automatic provisioning on the G Suite Connector, which will create all the users from O365 to GW with Office 365 identity on GW
- To ensure that all O365-backed Google accounts stay in one particular OU on GW, the fixed OrgUnit path attribute is mapped into the G Suite Connector
- On this OU, Auto License assignment was turned OFF to prevent override of any SKU other than Cloud Identity Free
- Enable Partial SSO on GW with Azure AD IDP URL(s) and certificate only on that OU
Acronyms
- GW = Google Workspace (users on Google Workspace with specific domain)
- O365 = Office 365 (users on Office 365 with specific domain)
- SA = Super Admin of Google Workspace
- GSPS = G Suite Password Sync (Windows Password sync from AD to Google)
- GCDS = Google Cloud Directory Sync (Unidirectional Users and other LDAP resources sync to Google)
- SKU(s) = type of Google Workspace License
- Partial Domain Licensing = single Google Workspace tenant having multiple SKU(s)
- AD = Active Directory
- DC = Domain Controller
- OU = Google Organization Unit containing the users
References
Hope this article helps you navigate identity challenges encountered in coexistence in your organization. If you have any questions, please leave a comment below.
Stay tuned for the next blog which will focus on Calendar-interop between Google Workspace and Office365. Thanks!
- Improve the security of your Google Workspace Environment: Protect users with BeyondCorp Enterprise
- Tips and resources to maximize your productivity with Gemini for Google Workspace
- Google Workspace Community Roundup: 2023 Year in Review!
- How to set up Google Workspace Federation with Microsoft Entra ID (Azure AD)
- Save time and effort with Google Workspace Domain Transfer for Google to Google migrations

 Twitter
Twitter